This section discusses the process of generating a keystore file, using it to create a Certificate Signing Request (CSR) for third party CA authorities, importing the signed certificates back into the keystore, and using it in Fiorano to create secure RESTful or Web services.
Generating a Keystore
Open command prompt and navigate to the %JDK_HOME%/bin directory.
Enter the following command, and then press Enter.
- Enter a password for the keystore. The password used in this example is "fioranopass".
- Provide the Organization details as prompted. When prompted for the First Name and Last Name, enter the fully qualified domain name (FQDN), Host Name or URL of the organization for which the certificate is applied for.
For requesting a Wildcard certificate, please add an asterisk * on the left side of the Common Name.
Example: .mydomain.com or www.mydomain.com. This secures all subdomains of the Common Name.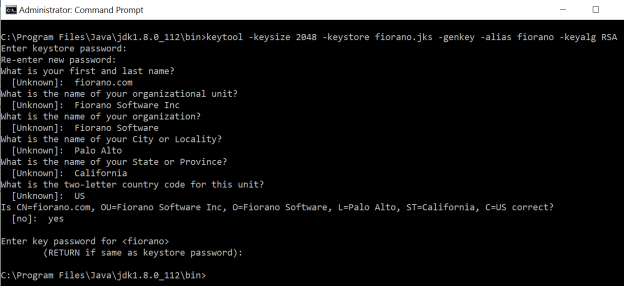
Generating a Certificate Signing Request (CSR)
A CSR needs to be generated using the keystore created in the previous section. This CSR is used by the CA authorities. Whenever a keystore is changed or updated, a new CSR needs to be generated.
To Generate a CSR, perform the actions below:
Enter the following command, and then press Enter:
- Provide keystore password (fioranopass) provided in the Generating a Keystore section above.
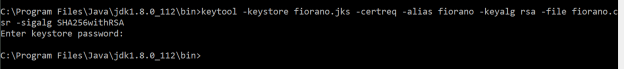
- A file named "fiorano.csr" gets created which contains the certificate signing request (CSR). This CSR has to be passed on to the external/third party Certificate Authority (CA).
The CA will authenticate the certificate requestor (usually off-line) and will return a certificate or certificate chain used to replace the existing certificate chain (which initially consists of a self-signed certificate) in the keystore.
Generating SSL certificate using CSR
A third-party CA website needs to be used to request an SSL certificate using the CSR generated in the Generating a Certificate Signing Request (CSR) section. Third party CA websites such as http://www.thawte.com/ and https://www.godaddy.com can be used to generate SSL certificates. In this example, a 21-day trial certificate of Thawte.com is generated and used. This trial certificate is not recommended to be used in the actual implementation.

To copy the CSR,
- Open the fiorano.csr file generated in the Generating a Certificate Signing Request (CSR) section.
- Highlight the area from ----BEGIN CERTIFICATE REQUEST to END CERTIFICATE REQUEST---- and press Enter.
- Paste it in the CA website online application to generate SSL certificates.
Using certificates from a CA authority
CA authorities will subsequently send a signed certificate, intermediate certificate and root certificate. Import all these certificates into the fiorano.jks keystore file.
The certificate will only work with the same keystore that was initially created with the CSR. The certificates must be installed to the keystore in the correct order.
Assuming sslcert.pem, intermediate.pem and root.pem are the certificates received from CA authorities, following commands are used to import all the certificates into the keystore.
![]()
![]()
![]()
All the certificates are added to the keystore and it is ready to use.
When root and intermediate certificates are added to the keystore, a message: "Certificate was added to keystore" is displayed. When the primary certificate is added to the keystore, a message "Certificate reply was installed in keystore" is displayed.
If there are no errors in this process, move to the Using the keystore in Fiorano section.
Listing keystore entries
To list the keystore and check if all the certificates are imported successfully, use the following command:
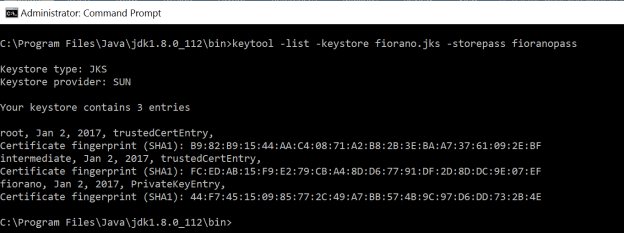
To display the certificate chain length for fiorano alias, specify the -v option in the above command.
