The LDAPLookup component enables the lookup of information organized in a directory-like fashion on a Lightweight Directory Access Protocol (LDAP) server. This information could be encryption certificates, pointers to printers and other services on a network, and provide a single logon facility where one password for a user is shared between many services. The adapter performs the LDAP client operations by connecting and authenticating to the server. The operations performed are bind, lookup, modify, add, delete, rename, change password.
Points to note
- In case of Authentication/Lookup/Binding failure, messages are sent to the output portwith the appropriate messages like Authentication failed/Lookup failed and so on... No message comes out onto the Error port.
- In the Lookup operation, when you enter the Root node (in CPS), the substring starting with 'dc' is checked against the substring starting with 'dc' of the string'SECURITY_PRINCIPAL' specified in Managed Connection Factory panel. In case of mismatch, an appropriate error message is shown. If it matches, the Base node and Filter is cleared.
- In the Bind operation, adding new attributes/ adding multiple values to an existing attribute can be achieved with the help of the attribute 'AdditionalAttribute'. Always make sure that 'cn' (at least one, if you are giving multiple 'cn's) holds the value of 'cn' given in 'dn'. Also make sure that 'sn' is provided if the value of 'objectClass' is 'person'. You can add multiple users at a time also.
- The source code for this component is available with the installer.
Configuration
Managed Connection Factory
Drag the LDAPlookup adapter present in the Samples section of the Micro Service Palette. Double-click the component from Fiorano Orchestrator to launch the configuration wizard.
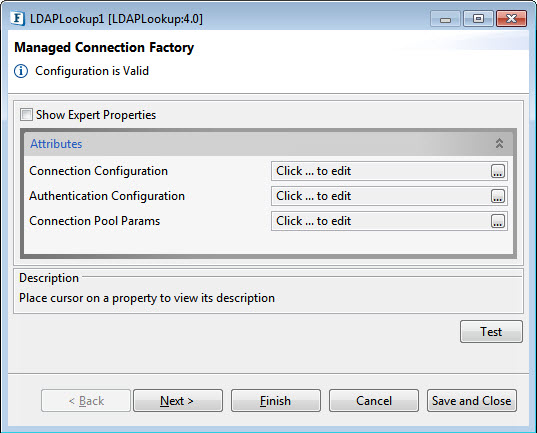
Figure 1: Managed Connection Factory
Connection Configuration
Click the ellipsis button to manage connection configuration properties.
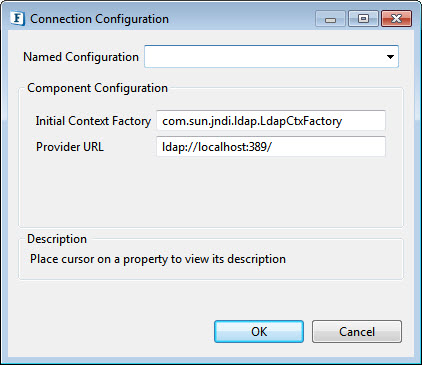
Initial Context Factory
Name of the environment property for specifying the initial context factory to use. The value is the fully qualified class name of the factory class that will create an initial context.
Provider URL
URL of the LDAP server.
Authentication Configuration
Click the ellipsis button to manage connection configuration properties.
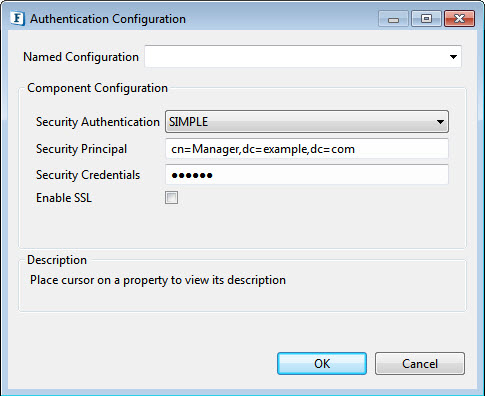
Security Authentication
Type of security authentication required. Apart from the default value—'SIMPLE', other options available are explained in the sections below.
NONE
Does not use a default Authentication.
SIMPLE
Security Principal: The distinguished name of the entry that is to be authenticated.
- Security Credentials: Password of the entry represented by 'Default Principal'.
CRAM-MD5
It has the same options as that of SIMPLE.
DIGEST-MD5
Below are the options apart from the ones present in SIMPLE:
- Authorization Id: The authorization Id for SASL mechanisms. If this property is not selected, ID will be derived from the client's authentication credentials.
- SASL Realm: The realm information required by SASL mechanisms. On selecting this, a mechanism-specific default is used.
GSSAPI
- Authorization Id: The authorization Id for SASL mechanisms. If this property is not selected, ID will be derived from the client's authentication credentials.
- krb5.conf Location: Path of the kerberos configuration file which contains the kerberos configuration information. If this property is not set, the default location is used.
- krb5 KDC: Kerberos KDC (Key Distribution Centre) used for the kerberos tickets.
- krb5 Realm: The default realm for kerberos.
- Login config file: The JAAS Login Configuration file.
EXTERNAL
The options Key Store Location, Key Store Type and Key Store Password gets added to the Attributes section.
Enable SSL
Specify if SSL is to be used during connection.
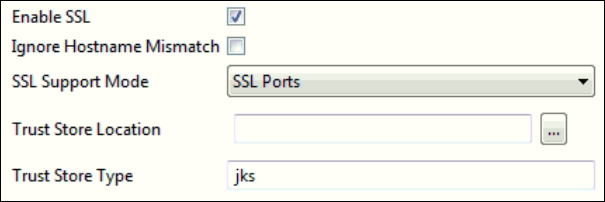
Figure 2: SSL properties
Ignore Hostname Mismatch
Specify if hostname mismatch in SSL certificate can be ignored to make connection.
SSL support Mode
Specify whether to enable SSL via SSL Ports or by using Start TLS extension in LDAP.
Trust Store Location
Location of the Trust Store
Trust Store Type
Provide type of the Trust Store; default value is "jks".
Security Principle
Specify the identity of the principal for authenticating the caller of the service.
Security Credentials
Specifies the credentials of the principal for authenticating the caller of the service.
Connection Pool Params
Various parameters to be used in connection pooling of EIS connection.
Refer to the Connection Pool Params section in the Common Configurations page.
Interaction Configurations
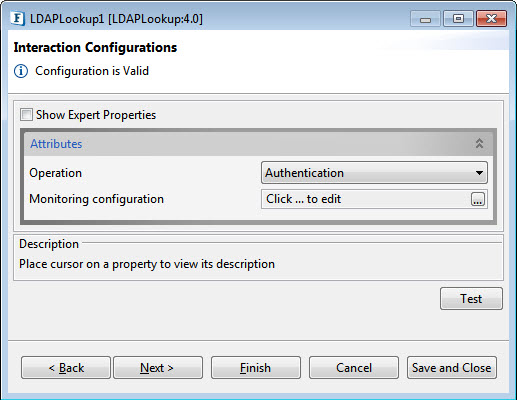
Figure 3: Interaction Configurations
Attributes
Operation
Choose the LDAP operation to be performed from the list of operations as below:
- Authentication
- Lookup
- Compare
- Bind
- Modify
- Delete
- Rename
- Change Password.
- Poll
There are separate attributes for different Operation options; each one is described below disabling Expert Properties as it appears the same for all options.
Authentication operation
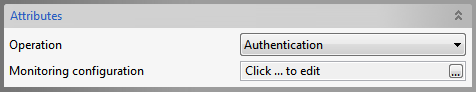
Figure 4: Authentication Operation Attributes
The component acts as an authenticator. The properties configured in the Managed Connection Factory panel are the ones required for authentication.
Lookup operation
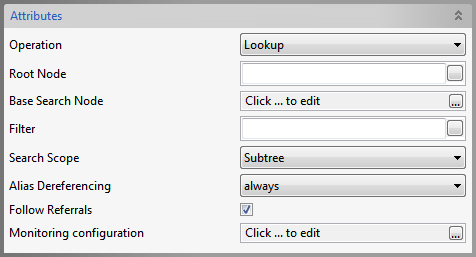
Figure 5: Lookup Operation Attributes
Root Node
Specify the Distinguished Name (DN) of an entry, the sub-tree of which you want to view in the editor that opens with the property.
Base Search Node
Choose the DN of the entry whose sub-tree and the entry by itself have to be searched for
Filter
Specify the search constraints to be applied on the entry represented by 'Base Search Node' and the entries in its sub-tree.
Search Scope
Specify the scope of the search.
Alias Dereferencing
Specify how aliases are to be dereferencing during search operation.
Follow referrals
Specify whether referrals are to be followed or ignored.
Compare operation
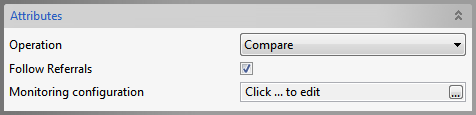
Figure 6: Compare Operation Attributes
Follow Referrals
Specifies whether referrals are to be followed or ignored.
Bind operation
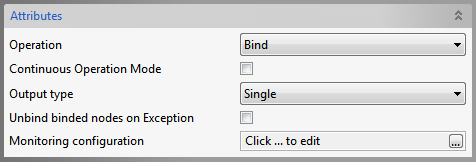
Figure 7: Bind Operation Attributes
Continuous Operation Mode
If true, operations on the subsequent nodes are continued if an exception occurs while processing some node, in case of processing multiple nodes in a single input. If false, operation is stopped if any exception occurs.
Output Type
Single- A single output for success of operations on all nodes. Multiple-Multiple outputs.
Unbind binded nodes on Exception
Specifies the action(Unbind already binded nodes/Leave them binded) when an exception occurs while adding some node.
Modify operation
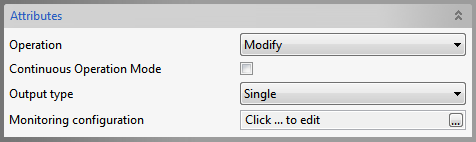
Figure 8: Modify Operation Attributes
Continuous Operation Mode and Output Type
Refer the Bind section above.
Delete operation
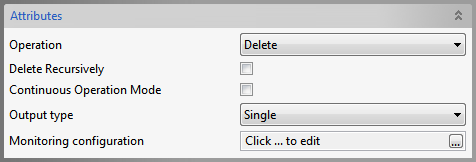
Figure 9: Delete Operation Attributes
Delete Recursively
Specifies whether a recursive delete must be done. If true, and if the DN specified isn't a leaf, its children and all their children are deleted are down the tree. If false, only the leaf entries are deleted
Continuous Operation Mode and Output Type
Refer the Bind section above.
Rename operation
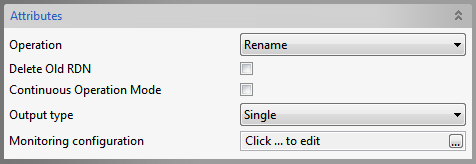
Figure 10: Delete Operation Attributes
Delete old RDN
Delete previous Relative Distinguished Name
Continuous Operation Mode and Output Type
Refer the Bind section above.
Change Password operation
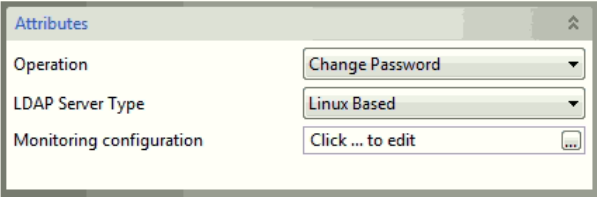
Figure 11: Change Password Operation Attributes
The properties configured in the Managed Connection Factory panel are the ones required for Change Password operation.
LDAP Server Type
- Linux Based: This includes servers where password can be transmitted as plain test. Example: OpenLDAP.
- Microsoft Active-Directory: Use this option when connecting to Microsoft Active-Directory where password is converted to UTF-16 and transmitted.
Poll operation
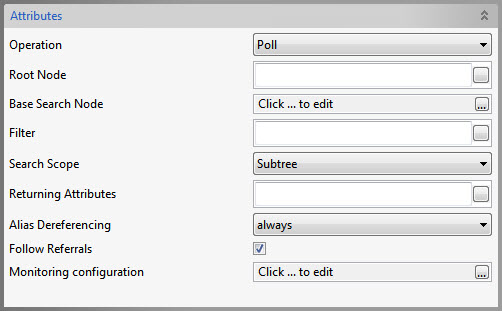
Figure 12: Poll Operation Attributes
Returning Attributes
Specify the list of attributes to be returned when a change occurs.
Monitoring Configuration
Refer to the Monitoring Configuration section in the Common Confirmation.
Expert Properties
Enable the Expert Properties view to configure these properties.
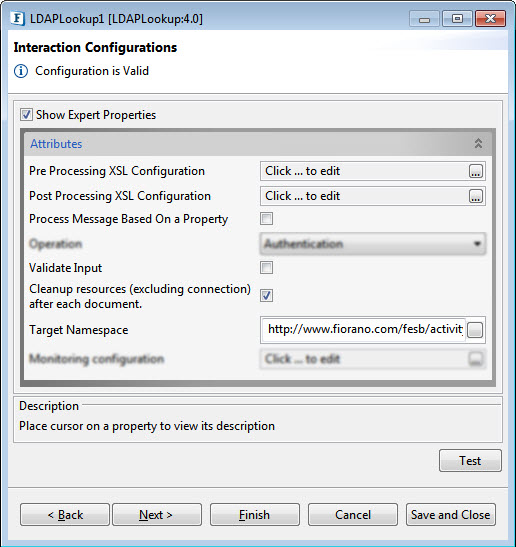
Figure 13: LDAPLookup CPS with the Expert Properties enabled and highlighted
Pre Processing XSL Configuration
Pre Processing XSL configuration can be used to transform request message before processing it. Click the ellipses button against the property to configure the properties.
Refer to the Pre/Post Processing XSL Configuration section under the Common Configurations page for details regarding Pre Processing XSL configuration and Post Processing XSL configuration (below).
Post Processing XSL Configuration
Post Processing XSL configuration can be used to transform the response message before sending it to the output port.
Process Message Based on Property
The property helps components to skip certain messages from processing.
Refer to the Process Message Based On a Property section under the Common Configurations page.
Validate Input
If enabled, LDAPLookup validates the input received.
Cleanup resources (excluding connection) after each document
This closes all the resources except for the connection after every request. If the less processing time is more important than the less memory usage, then it is recommended to disable this property and vice versa.
For more details, refer to the respective section under in the Common Configurations page.
Target Namespace
Target Namespace for the request and response XML messages.
For more details, refer to the respective section under in the Common Configurations page.
Scheduler Configurations
On enabling scheduling, we can set the repeat interval in milliseconds/seconds/hours/minutes/days unit and the repeat period can be set as Repeat forever or the number times can be specified too as an alternative.
Another scheduling option is to set the start time and date which helps to control the start of scheduling process.
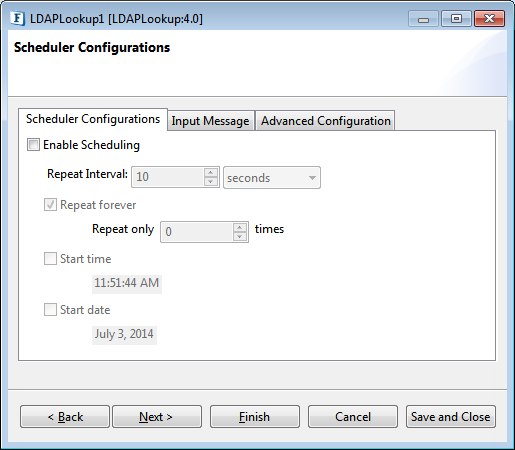
Figure 14: Scheduler Configurations
Please refer Scheduler Configurations section in the Common Configurations page.
Transport Configurations
Transport Configurations panel is used to configure messaging properties when the component is configured in Scheduling mode.
Figure 15: Transport Configurations
Please refer to the Transport Configurations section in the Common Configurations page.
Error Handling Configuration
The remedial actions to be taken when a particular error occurs can be configured here. Click the ellipsis button against this property to configure Error Handling properties for different types of Errors. By default, the options Log to Error Logs and Send to error port are enabled
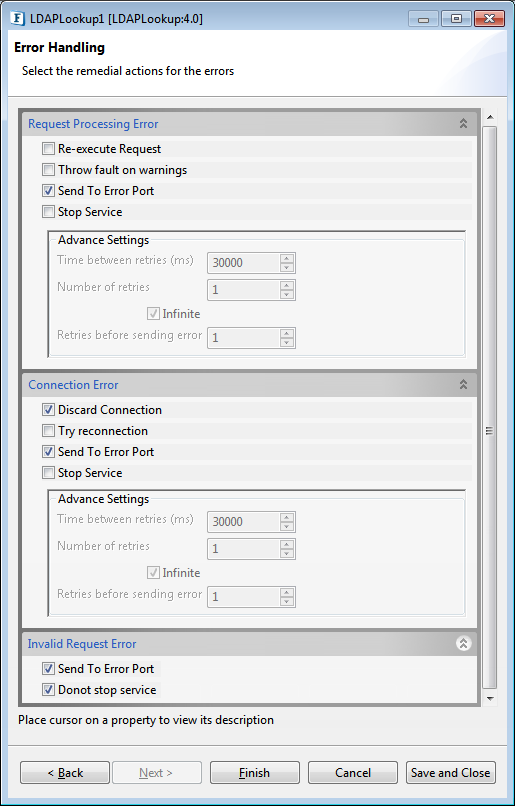
Figure 16: Error Handling Configurations
Functional Scenario
Sample 1: Bind Configuration
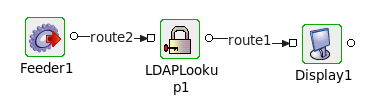
Figure 17: LDAPlookup event flow
- Connect the LDAPLookup1 adapter to a Feeder and a Display as shown in the figure above.
- Launch the configuration wizard by double-clicking the LDAPlookup icon in the Fiorano Orchestrator.
- Set the fields in the Managed Connection Factory configuration page as shown in Figure 1.
- Choose the Operation as 'Bind' in Interaction Configuration panel.
- Save and close the wizard and open feeder CPS.
To create a user in the server, enter the following in the feeder :
- Perform CRC (resource and connectivity) and then launch the event process. This will create a new user in the 389-ds server.
Sample 2: Lookup configuration
- Follow steps 1-3 from sample 1.
- Choose the Operation as 'Lookup' in Interaction Configuration panel.
- Provide the following values:
- Root Node: dc=localdomain
- Filter: cn=Directory Manager,dc=localdomain
- Save and close the LDAPLookup CPS and open the Feeder CPS.
Copy the following and specify the filter .
Perform CRC and launch the event process. This will display all the details of the user.
Sample 3: Authentication Configuration
- Follow steps 1-3 from sample 1.
- Choose the Operation as 'Authentication' in Interaction Configuration panel.
- Click the Test button.
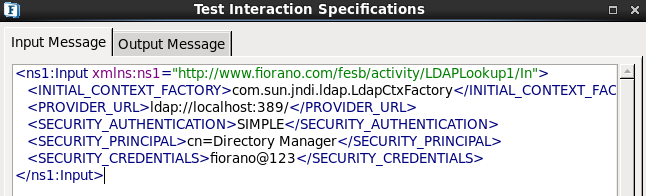
Figure 18: Authentication Configuration - Enter the above details in the Input Message tab.
- Click the Validate button and then click the Execute button to get the following result.
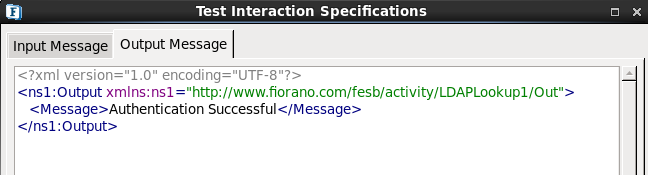
Figure 19: Authentication Configuration Result
Sample 4: Change Password Configuration
- Follow steps 1-3 from Sample 1.
- Choose the Operation as 'Change Password' in Interaction Configuration panel.
- Click the Test button.
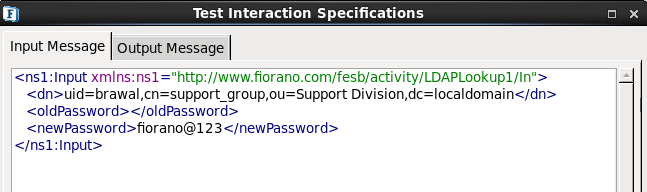
Figure 20: Password Change Configuration
- Specify the Distinguished Name, old password and new password
- Click Validate then click Execute to get the following result.
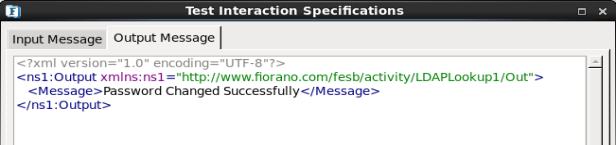
Figure 21: Password Change Configuration – Result
Sample 5: Delete Configuration
- Follow steps 1-3 from Sample 1.
- Choose the Operation as 'Delete' in Interaction Configuration panel.
- Click the Test button.
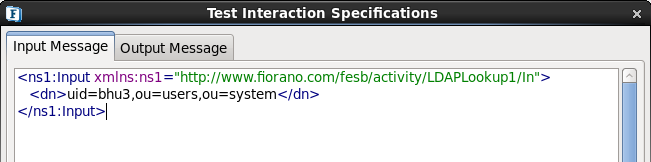
Figure 22: Delete Configuration specify-dn
- Specify the distinguished name of the entry to delete.
- Click Validate and then click Execute to get the following output.
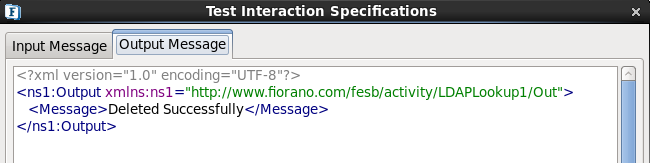
Figure 23: Delete Configuration - Result
Sample 6: Rename Configuration
- Follow steps 1-3 from Sample 1.
- Choose the Operation as 'Rename' in Interaction Configuration panel.
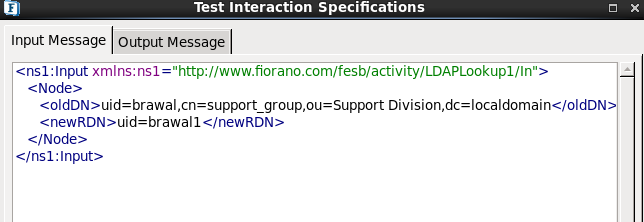
Figure 24: Rename Configuration
- Enter the old Distinguished Name and the new relative distinguished name.
- Click Validate and click Execute to get the following result.
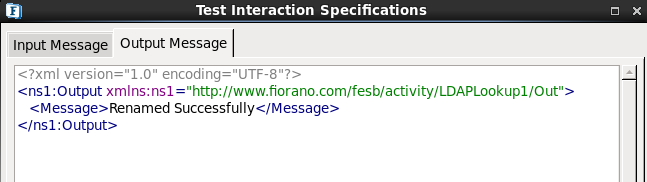
Figure 25: Rename Configuration - Result