Using Authentication Modules to Authenticate a User
The implementation details with respect to interaction with the external security service provider (e.g: creating JDBC and SSL-enabled LDAP connections, querying the RDBMS/LDAP-provider to validate the user authentication information etc.,) to generate the required authentication information (passed/failed) must be done externally using the JAAS modules. The Fiorano Server calls these APIs to get the required authentication information and based on the results, authenticates the user for performing one of the above operations. This section discusses how the necessary plug-in modules need to be provided for the purposes of authentication.
Enabling JAAS Modules
To enable External Authentication, perform the following steps:
- Open Enterprise Server Profile in eStudio and go to Fiorano > security > SecuritySubSystem and check the UseAuthenticationModule checkbox.
- Enter the configurationName and configurationFileName as shown below:
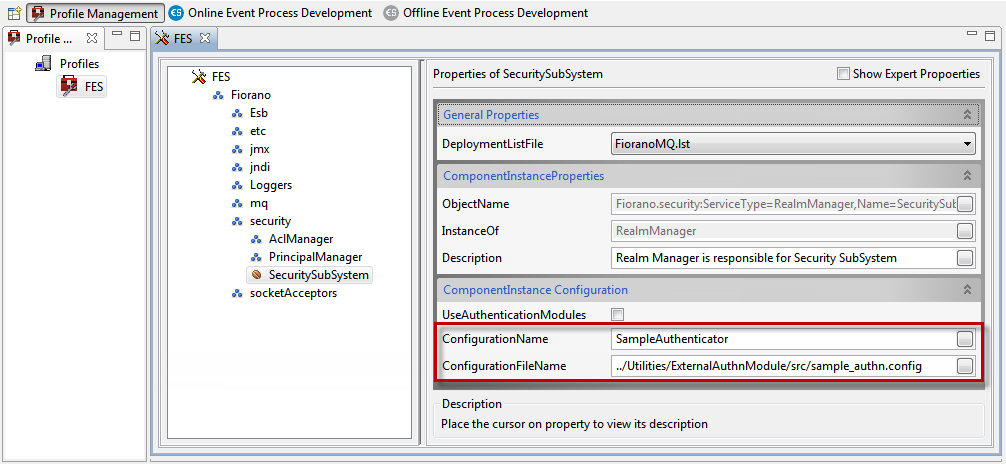
Figure 1: Entering configurationName and configurationFileName
An implementation for a particular authentication technology to be used via LoginModule(s) is determined at runtime. The implementation is specified in a login configuration file.
LoginModule
The LoginModule describes the interface implemented by authentication technology providers (system administrators). LoginModules are plugged in with applications to provide a particular type of authentication. While Fiorano invokes the LoginContext API, authentication technology providers should implement the LoginModule interface. As mentioned in previous section, the Configuration specifies the LoginModule(s) to be used with a particular login application (such as the Fiorano server). Therefore, different LoginModules can be plugged in seamlessly under the Fiorano server without any server-side configurations.
A sample LoginModule must implement the following methods of the javax.security.auth.spi.LoginModule:
- boolean abort()
- boolean commit()
- void initialize(Subject subject, CallbackHandler callbackHandler, Map sharedState, Map options)
- boolean login()
- boolean logout()
Once the implementations of the LoginModule interface are done, these must be included in the class path of Fiorano Server so that the LoginModules (as per configuration) are invoked successfully when the server invokes the LoginContext API while authenticating the user credentials. This should be done as follows:
- Locate the jar file which contains the class files of the implementation classes of the LoginModule.
- Open the %FIORANO_HOME%/esb/server/bin/server.conf file and add a line specifying the location to the above jar file.
Example Implementation
A detailed explanation and an example implementation of the LoginModule com.fiorano.jms.auth.SampleLoginModule is provided in
%FIORANO_HOME%/fmq/Utilities/ExternalAuthnModule directory.
More details of the class and other dependencies are present in the readme file located in the same directory.
Configuration File
In this file, mention the Module to be used for Authentication. For instance, a configuration file may contain the following content:
Providing External User credentials
If the specified LoginModule implementation has options that can be set, any desired option values may be specified here. This is a space-separated list of values which is passed directly to the underlying LoginModule. Options are defined by the LoginModule itself and control the behavior within it.
Admin User
When external authentication is used, creating an admin user in the external security service provider is not mandatory. The external user being used must be mentioned in the FES profile configuration at Fiorano > Esb > Transport > FESTransportmanager > MQProvider as shown in the figure below.
Mention credentials in the UserName and Password properties in the Properties of MQProvider panel. The server will create this user internally with administrative rights. This user can be used for doing any administrative changes.
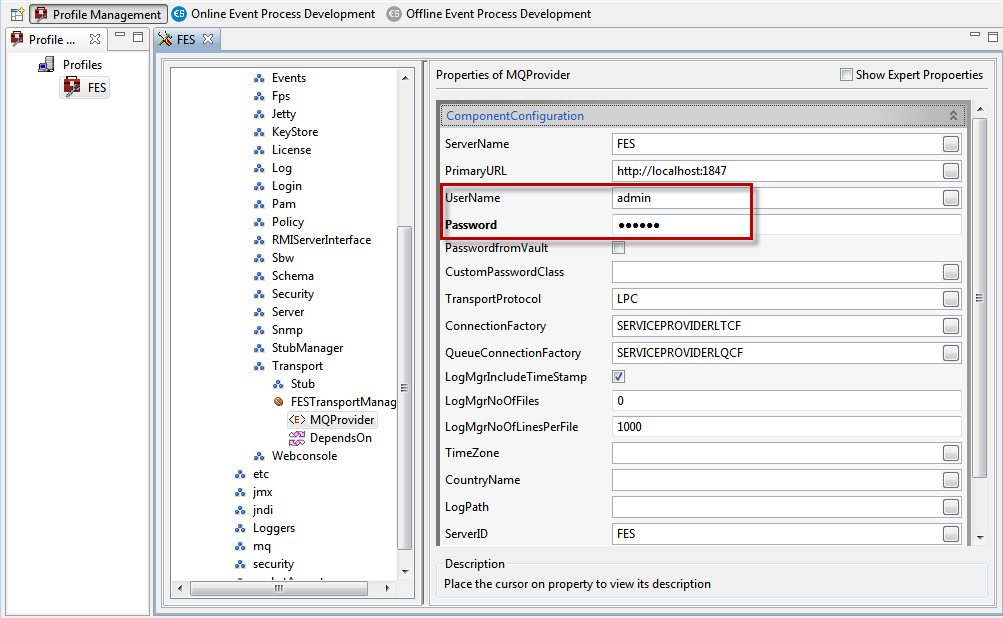
Figure 2: Providing MQProvider properties credentials
External User
The external user credentials (used in connecting FPS with FES) should be provided in FPS profile configuration at Fiorano > ESB > Peer > Transport > FPSTransportManager > EnterpriseServer as shown in the figure below.
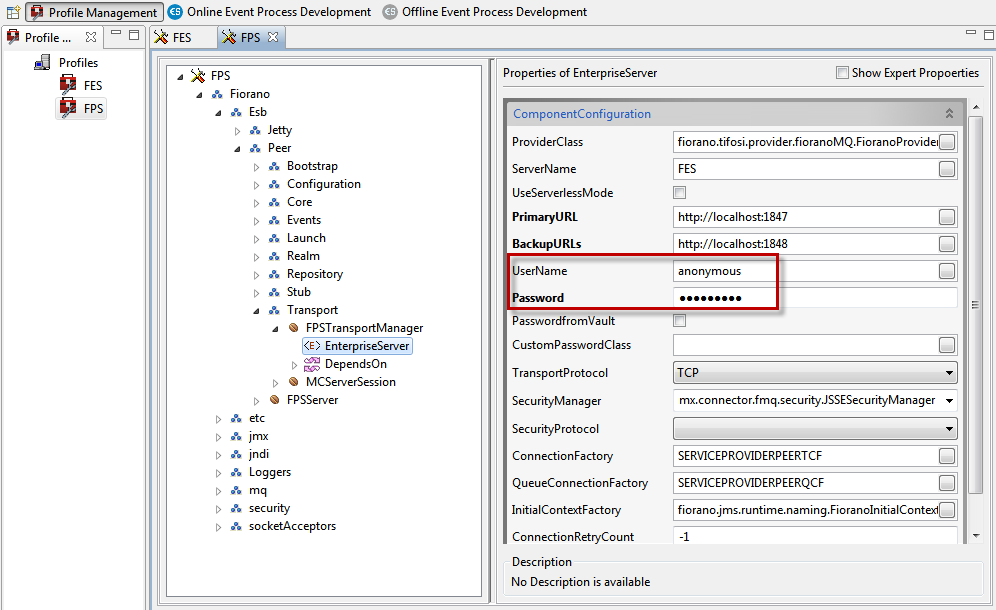
Figure 3: Providing external user credentials in FPS profile configuration
Password from Vault
If passwords are periodically changed in the security Database, the PasswordFromVault option can be used instead of changing the Password every time . If the PasswordFromVault check box is set, a 'key' replaces the password that is entered in the Password text field(s). The Java Class which implements ICustomEncryptor has to be specified in the CustomPasswordClass text box.
getPasswdFromVault (String key) method from CustomClass (the implementor of the IcustomEncryptor interface) gets the passwords by taking keys as parameters.
Below is the sample class that gets the password(s) from map collection, which stores passwords against keys. CustomPasswordClass should be included in the class path of the Fiorano Server as follows:
Compile the CustomPasswordClass java file with the fiorano-utilj4 jar file included in the classpath.
Open FIORANO_HOME/esb/server/bin/server.conf file, add a line specifying the location to jar file containing the above CustomPasswordClass.
Sample implementation of ICustomEncryptor
Points to note
- When external authentication is enabled for the FES, it must also be enabled for all Peers connected to the FES. Otherwise, Principal Store Synchronization will fail. To enable external authentication in each FPS, go to Fps > Fiorano > security > SecuritySubSystem and check UseAuthenticationModule checkbox. Fill in the configurationName and configurationFileName.
- When external authentication is enabled, the Security Datastore Reset option in dashboard will be disabled. On reset, users will be deleted and default users are created. This compels to store default users in an external security system. In order to avoid this constraint, the Security Datastore Reset option is disabled.