The AS4 connector allows you to send and receive payloads via the AS4 messaging protocol. The AS4 connector is compliant with the AS4 minimal client conformance profile defined in the AS4 profile of ebMS 3.0. It allows exchanging any type of payload (e.g., XML, JSON, Binary) as SOAP attachments or SOAP body payloads.
Configuration and Testing
Component Configuration
The component can be configured using the Configuration Property Sheet (CPS) as explained in the following sections.
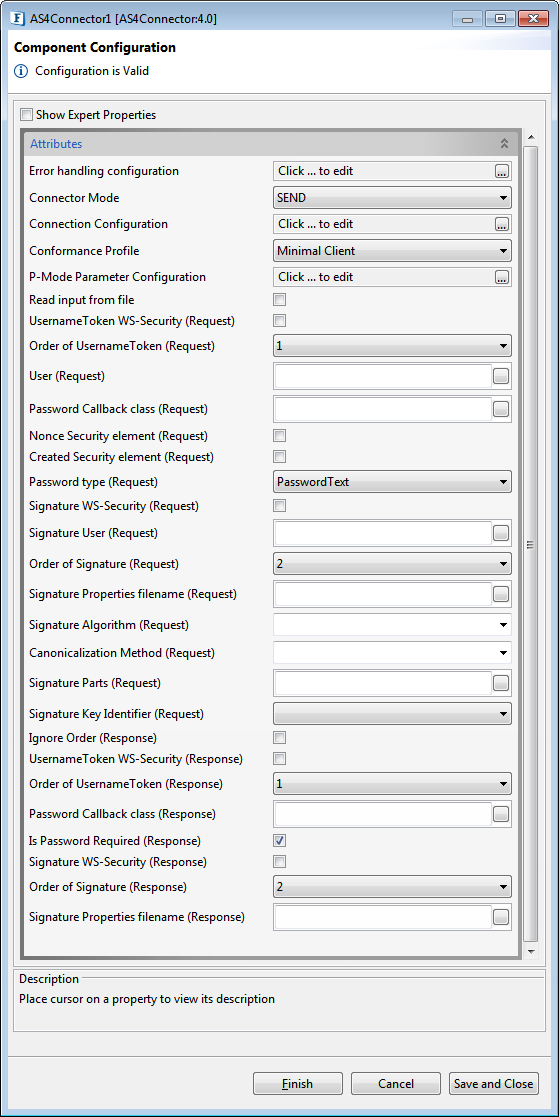
Figure 1: Connection configuration details
Error Handling Configuration
The remedial actions to be taken when a particular error occurs can be configured using this attribute.
Click the ellipsis button against this property to configure Error Handling properties for different types of Errors.
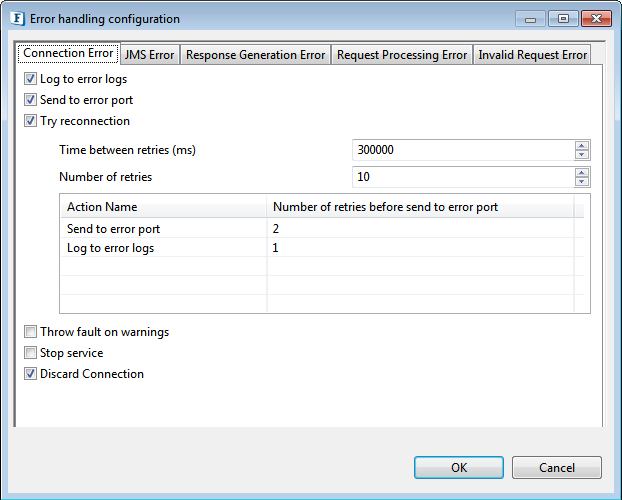
Refer to the Error Handling section in Common Configurations for detailed information.
Connector Mode
Send
The AS4Connector acts as a client and sends an AS4 message to a messaging services handler(MSH).Receive
The AS4Connector acts as a server and receives an AS4 message from a messaging services handler(MSH). If the message is valid the payload is saved and a receipt is sent back to the MSH else an error signal is sent back to the MSH.
Service Name
The service name assigned to the AS4 Server instance. It specifies the service name to which the client has to send the message.
When deployed, a URL is assigned in the following format:
Connection Configuration
Click the ellipsis button against this property to edit connection configuration.
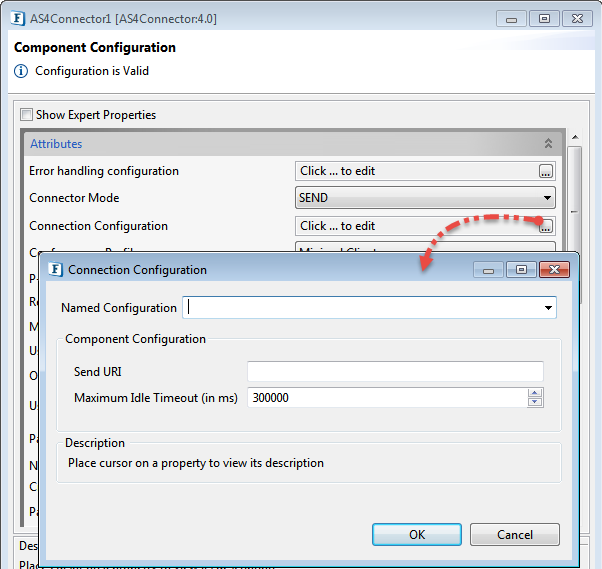
Send URI
Endpoint Address where the service is hosted in the Target EBMS server.Maximum Idle Timeout
It is the maximum time (in milliseconds) till which a connection exists between the server and client without sending a request.
Conformance Profile
Specifies Conformance Profile to be implemented.
Minimum Client
It provides security features while sending and receiving AS4 MessagesLight Client
To send and receive AS4 Messages. This is an entry level conformance profile meant for medium to larger volume data exchanges.
P-Mode Parameter Configuration
Click the ellipsis button to configure P Mode parameters.
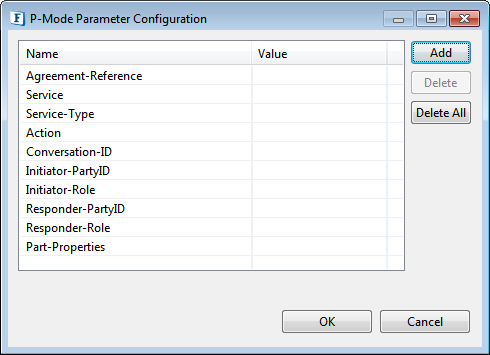
| Name | Description |
| Agreement-Reference | This element contains the identification of the business level agreement between the trading partners. |
| Service Name | This element contains the meta-data on the business service that is [supposed] to handle the user message. |
| Service Type | |
| Action | This element contains the business level operation/activity requested to be executed |
| Conversation ID | This element is a string identifying the set of related messages that make up a conversation between Parties. |
| Initiator Party ID | This element includes the information on the Initiator of the MEP, i.e. the partner that sends the first ebMS message. |
| Initiator Role | The business role the partner is acting in.(i.e) Party Sending |
| Responder Party ID | This element includes the information on the Responder of the MEP. The information is the same as for Initiator. |
| Responder Role | The business role the partner is acting in.(i.e) Party Receiving |
| Part Properties | This element contains the information about the mime-type of the document which is transferred between the trading partners. |
Read input from file
If enabled, it allows the client to send different types of payload (to the target EBMS server) retrieved from a file that may be referred to using the following properties.
Attachment Directory
It is the directory where the payload file is saved.Attachment File
It is the file containing payload details.
Mime Type
Specify the format of the Payload from the below:
- text/xml
- text/plain
- image/jpeg
- application/octetstream
UsernameToken WS-Security (Request):
If the web service performs UsernameToken identification for the request, then this property should be enabled. Username and password values are added to the message headers.
Order of UsernameToken (Request):
Determines the order of the UsernameToken security function. The order of a security function determines when this function will be applied when multiple security functions are being used.
User
This property is used as the username for the UsernameToken security function. It is also used as the alias name in the keystore to get user's certificate or private key to perform signing for the Signature security function in case of "Signature User" is null and "Signature WS-Security (Request)" is set to yes. It is also used as the fallback for the encryption security function in case of "Encryption User" is null and "Encryption WS-Security (Request)" is set to yes.
Password Callback class (Request)
This is needed by the security functions to get the password and to verify the username/password pair. The password callback class should implement javax.security.auth.callback.CallbackHandler class. This Password Callback class should be the fully qualified name of the class. The jar which contains the password callback class should be added as a resource to the component.
- Password type: The Password type specifies how the client sends the password value to the server.
- PasswordText: Password is sent in raw text format within the security header of the soap request.
- PasswordDigest: Password is sent in digest format within the security header of the soap request.
- PasswordNone: No password will be sent in the security header. This option is useful when the user wants to specify the username without any password.
Nonce Security element
Specifies whether to use nonce element in the security header or not. When UsernameToken security function is used, then nonce security element can be employed to prevent message replay attacks. A nonce is a random value that the client creates to include in each UsernameToken that it sends. Although using a nonce is an effective countermeasure against replay attacks, it requires the server to maintain a cache of used nonces, consuming server resources.
Created Security element
Specifies whether to use Created element in the security header or not. This element denotes the time of creation of a nonce. Combining a nonce with a creation timestamp has the advantage of allowing a server to limit the cache of nonces to a "freshness" time period, establishing an upper bound on resource requirements.
Signature WS-Security (Request)
If this security function is selected the digest of the message is created and encrypted before sending. The property "User" must be specified to get the private key/certificate of the respective user from the keystore for signing.
Order of Signature (Request)
Specifies the order of the Signature security function. The order of a security function determines when this function will be applied when multiple security functions are being used.
Signature User
This name is used as the alias name in the keystore to get user's certificate and private key to perform signing. If this parameter is not set, then the signature function falls back to the "User" parameter to get the certificate. Password for the user to get certificates from the keystore should be provided in the Password Callback class.
Signature Properties filename (Request)
The name of the crypto property file to use for SOAP Signature. Please see the description of "Encryption Properties filename" for the details of the properties file.
Signature Parts
The parameter specifies which parts of the request shall be signed. Please see the description of "Encryption Parts" for the syntax.
Signature Algorithm (Request)
The parameter specifies signature algorithm to be used. If an algorithm is not specified then the algorithm "http://www.w3.org/2000/09/xmldsig#rsa-sha1" will be used by default.
Canonicalization Method
The parameter specifies the canonicalization method to be used in the process of signing the request. If no method is specified then the method "http://www.w3.org/2001/10/xml-exc-c14n#" will be used by default.
Signature Key Identifier
Select the key identifier type to use. Please see the description of "Encryption Key Identifier" for the descriptions of key identifiers.
Ignore Order
If this is set, Order of Security actions will be ignored for the incoming response.
UsernameToken WS-Security (response)
Determines whether the response from the server contains Username token headers or not.
Order of UsernameToken (response)
Determines the order of the Username Token security function. The order of a security function determines when this function will be applied when multiple security functions are being used.
Password Callback class (response)
This is needed by the security functions to get the password and to verify the username/password pair. The password callback class should implement javax.security.auth.callback.CallbackHandler class. This Password Callback class should be the fully qualified name of the class. The jar which contains the password callback class must be added as a resource to the component.
Is Password Required
This property should set to false if the Username security token is used without a password. No need to provide Password callback class if this property is set to no.
Signature WS-Security (response)
Specifies whether the soap response or some parts of the soap response are signed or not.
Order of Signature (response)
Specifies the order of the Signature security function. The order of a security function determines when this function will be applied when multiple security functions are being used.
Signature Properties filename (response)
The name of the crypto property file to use for SOAP Signature. Please see the description of "Encryption Properties filename (Request)" for the details of the properties file.
Functional Demonstration
Scenario 1
Sender Configuration
Receiver Configuration
Output