XMLSecurityProvider is used for encrypting and signing the XML data.
The Configuration Property sheet (CPS) provides an option to choose elements for encryption/decryption.
Configuration and Testing
Component Configuration
The component has the following attributes which can be configured from the CPS (Configuration Property Sheet) below.
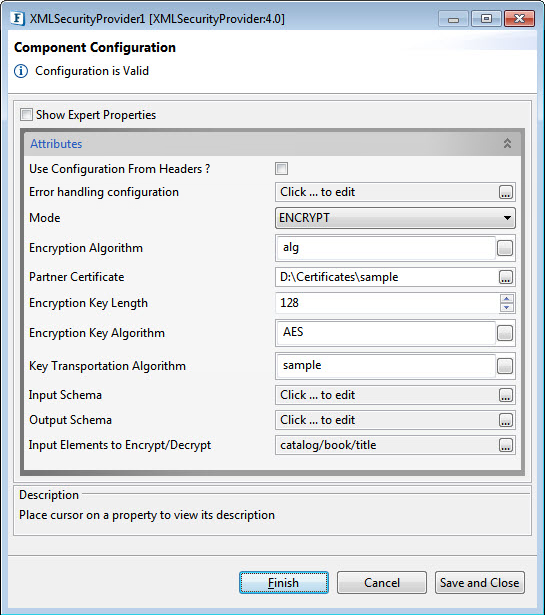
Figure 1: Configurable properties of XMLSecurityProvider component
Use Configuration From Headers
If enabled, values from Headers will be prioritized over the CPS values; attributes are hotkeystore, partnerCertificate, hostPrivateKeyPassword, hostStorePassword, hostKeyStoreAlias, encryptionKeyAlgorithm, keytransportationalgorithm, encryptionalgorithm, signingAlgorithm, encryptionKeyLength.
Error handling configuration
The remedial actions to be taken when a particular error occurs can be configured using this attribute.
Click the ellipsis button against this property to configure Error Handling properties for different types of Errors.
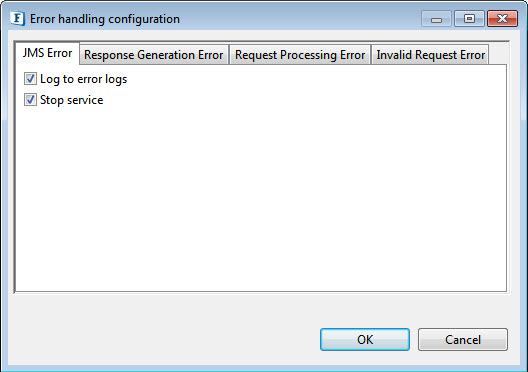
Figure 2: Error handling configuration properties
Refer Error Handling section in Common Configurations for detailed information.
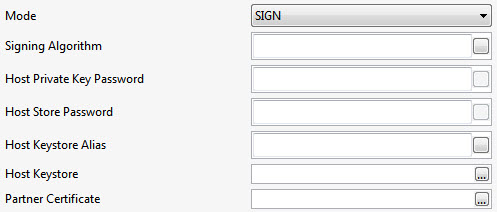
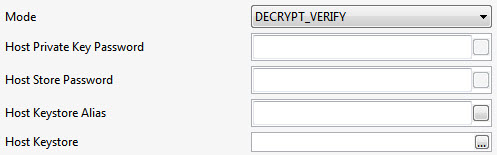
Mode
Operations available in the component. The modes available are described in the table below.
| Mode | Description |
ENCRYPT | Used to encrypt the data with given credentials using a host certificate. (see the figure above) Encryption AlgorithmAlgorithm to be used for encrypting data. Partner CertificatePartnerCertificate path representing the alias. Encryption Key LengthLength of the encryption key to be generated. Encryption Key AlgorithmThe private key is encrypted once again to strengthen security measures. This is the algorithm which is to be used for encrypting the private key. Key Transportation AlgorithmTransport Algorithm takes a different approach that provides higher security assurance, by encrypting a random integer with the recipient's public key and using a symmetric key-wrapping scheme to encrypt the keying data. |
SIGN | Creates a signature using a private key.
Signing AlgorithmAlgorithm to be used for Signing the data. Host Private Key PasswordPassword for the private key. Host Store PasswordPassword for the keystore used. Host KeyStore AliasAlias name given for the keypair entry in the keystore. Host KeyStoreKeystore path which contains KeyPair. Partner CertificatePartnerCertificate path representing the alias. |
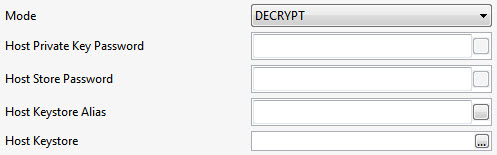
DECRYPT | Used to decrypt the selected elements by the hosts private key.
|
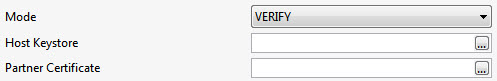
VERIFY | Used to verify the authenticity of the received message. If the file does not come from the expected source, that is, if the signature does not match or if it is tampered, an error gets logged.
Host KeyStoreKeystore path which contains the KeyPair. |
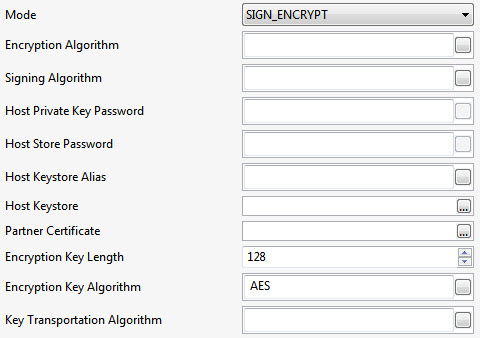
SIGN_ENCRYPT | Encrypts the data and produces the signature.
Encryption AlgorithmAlgorithm to be used for encrypting the data. |
DECRYPT_VERIFY | Decrypts the data and verifies the signature received.
|
Input Schema
Provide the schema used for generating XML data. Click the ellipsis button and add schema from the dialog box.
Output Schema
Provide the schema for the output message.
Input Elements to Encrypt/Decrypt
Click the ellipsis button to add elements to encrypt/decrypt.
Elements get auto-populated based on the Input/Output Schema provided. Select the elements to encrypt/decrypt and click the arrow button to choose those. These elements will be used for encryption and signing.
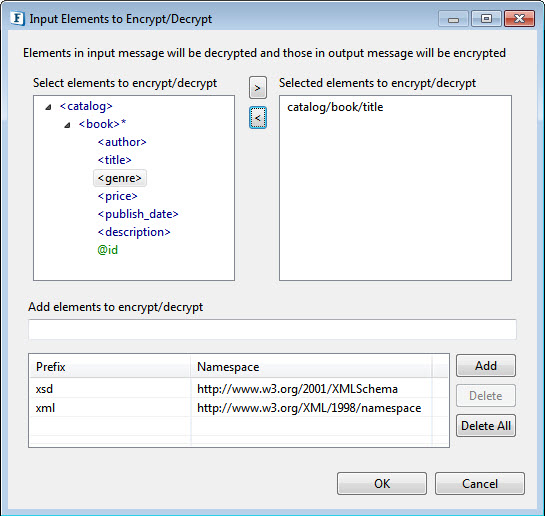
Figure 6: Dialog box to add elements for encryption/decryption
Add elements to encrypt/decrypt
Some components may not have schema on ports. In that case, semicolon separated XPaths can be provided here.
Namespace Prefixes: A map of prefix versus namespace used in XPaths can be configured here.
Expert Properties
Enable the Expert Properties view to configure these properties.
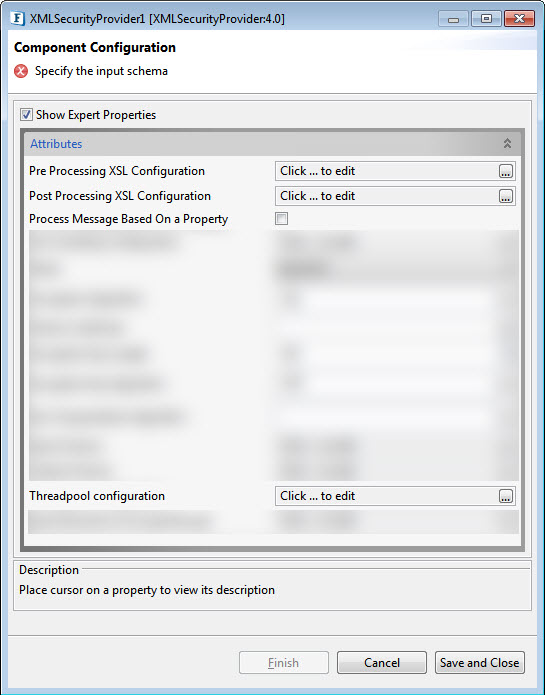
Figure 7: Expert properties for Generate sequencer mode
Pre Processing XSL Configuration
Pre Processing XSL configuration can be used to transform request message before processing it. Click the ellipses button against the property to configure the properties.
Refer to the Pre/Post Processing XSL Configuration section under the Common Configurations page for details regarding Pre Processing XSL configuration and Post Processing XSL configuration (below).
Post Processing XSL Configuration
Post Processing XSL configuration can be used to transform the response message before sending it to the output port.
Process Message Based on Property
The property helps components to skip certain messages from processing.
Refer to the Process Message Based On a Property section under the Common Configurations page.
Threadpool Configuration
This property is used when there is a need to process messages in parallel within the component, still maintaining the sequence from the external perspective.
Click the Threadpool Configuration ellipsis button to configure the Threadpool Configuration properties.
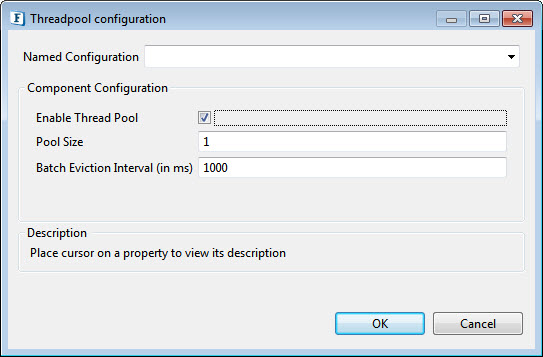
Figure 8: Threadpool Configuration
Enable Thread Pool
Enable this option to configure the properties that appear as below.
Pool Size
Number of requests to be processed in parallel within the component. Default value is '1'.
Batch Eviction Interval (in ms)
Time in milliseconds after which the threads are evicted in case of inactivity. New threads are created in place of evicted threads when new requests are received. Default value is '1000'.
Functional Demonstration
In the flow shown in the figure below, XMLSecurityProvider1 is configured with SIGN_ENCRYPT and XMLSecurityProvider2 is configured with DECRYPT_VERIFY. The Input XML is fed-in using the Feeder component. Display components are connected in such a way that the encrypted data from XMLSecurityProvider1 gets displayed in Encrypted display component and decrypted data from XMLSecurityProvider2 gets displayed in Decrypted display component.
Title element is selected for encryption in the following scenario.
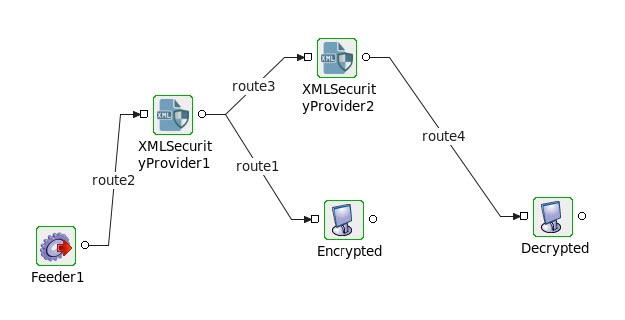
Figure 9: Sample event process to demonstrate XMLSecurityProvider functionality
Input
Below is the Input XML.
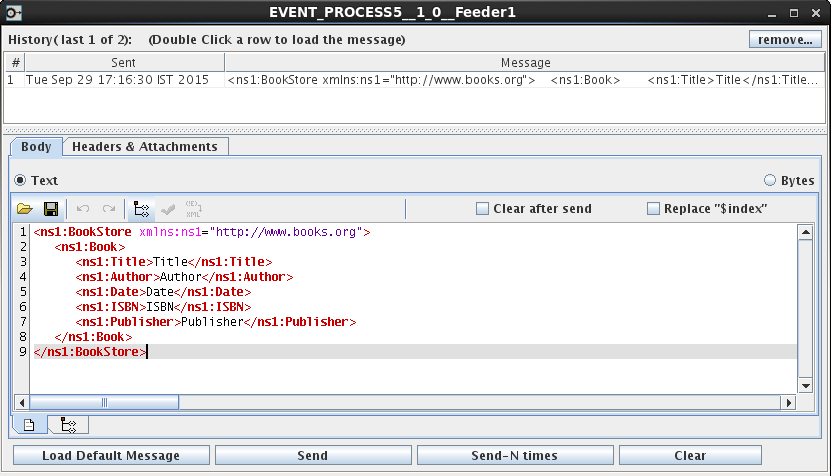
Figure 10: Sample Input XML
Output
Encrypted Output
The encrypted output for the input XML provided is as shown in the figure below.
Notice that dsig:Signature tag consists of algorithm digest data and all the algorithms used for operations. These would be collected by the receiver to extract the digest and verify the things. Title is encrypted as it was selected for encryption.
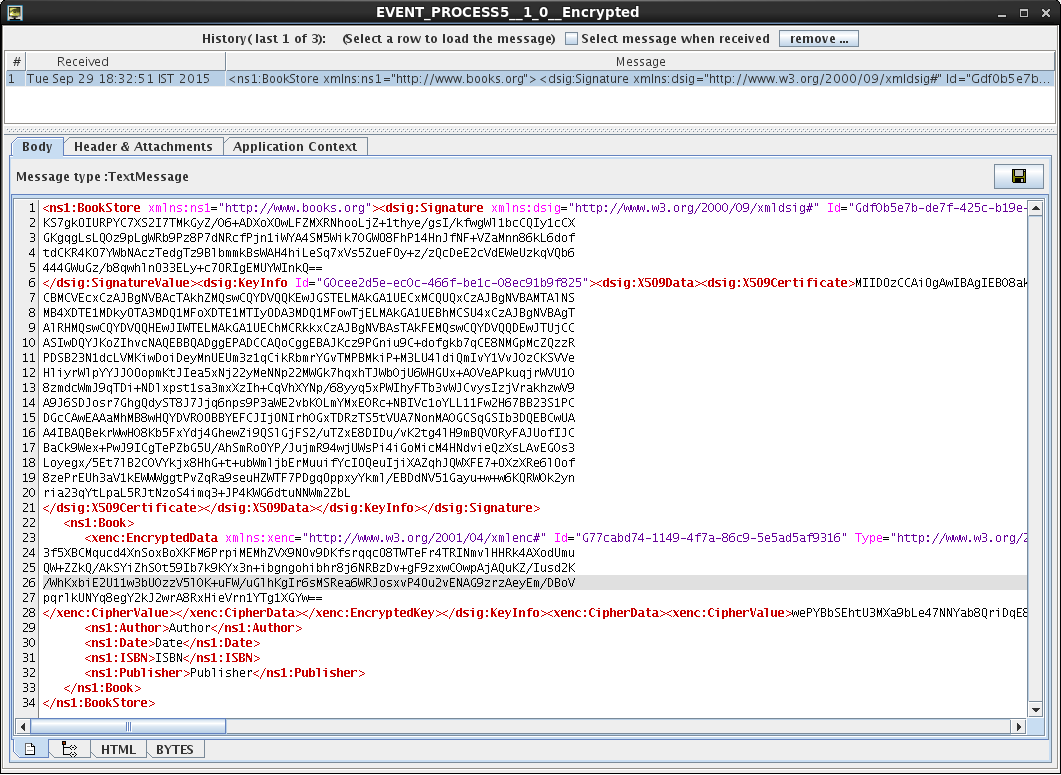
Figure 11: Output for the encrypted data displayed in the Encrypted Display window
Decrypted Output
The final Decrypted and verified (successful) output is displayed in the Decrypted display. The value of Title gets retrieved back.
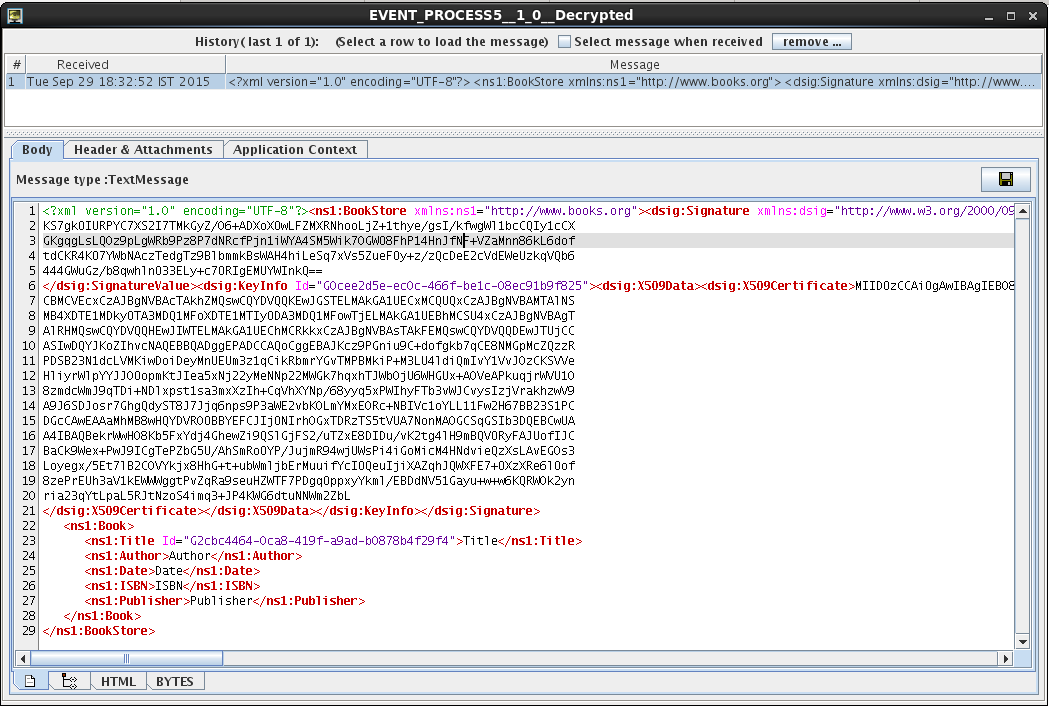
Figure 12: Output for the decrypted data displayed in the Decrypted Display window
Points to Note
If the launch mode is changed to 'Group Process', then the following argument needs to be added to the JVM_PARAMS property of the group process ID specified in XMLSecurityProvider: