Disk Level Encryption
Destination Encryption allows storage of sensitive data from different publishers in a secured way. Encryption implies the transformation of plain text into cipher text or vice-versa by using key.
Destination Encryption Characteristics
In Destination Encryption, all messages sent to a particular destination (topic or queue) are encrypted, thus providing a secure channel of delivery. A component does not have to encrypt the message explicitly like in Message Encryption. A destination is marked as encrypted at the time of its creation. All messages published on this destination are encrypted before storing those in the database and delivered decrypted to subscribing applications. A client application, therefore, does not have to explicitly decrypt a received message.
Base Implementation
Fiorano versions above 9.5.0 support Destination Encryption. DES (Data Encryption Standards) is used as the default encryption algorithm. In addition to that, Fiorano supports Base64, TripleDES, AES256, AES128, AES192, RC2-40, RC2-64, and RC2-128 standards too.
The Destination Encryption function uses the library cryptix.jar provided by Cryptix for generating keys as well as for encryption. This file comes bundled with the Fiorano installation. It can be found in the FIORANO_HOME/extlib/cryptix directory of the installation.
Destination Encryption involves only encrypting the payload of the message and not its JMS headers and properties.
Encrypted Destination Creation
Input/Output port properties appear in the Properties pane when an input port of a component instance is selected. Encryption properties can be configured in the input/output ports from the JMS Destination tab under the Properties panel.
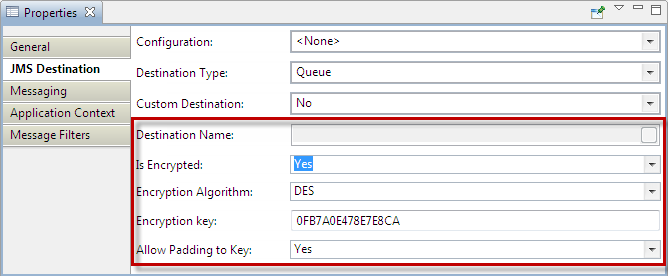
Figure 1: JMS Destination Port Encryption Configuration
- Is Encrypted:
- Yes – Encrypted JMS destination will be created.
- No – Non-Encrypted JMS destination will be created.
- Encryption Algorithm: The supported algorithms are DES, Base64, TripleDES, AES256, AES128, AES192, RC2-40, RC2-64, and RC2-128.
- Encryption Key: Specify key which is used to encrypt the incoming data. Specify 64 digit key for AES256, 48 digit key for AES192, 32 digit key for AES128, 16 digit key for DES, 48 digit key for TripleDES, 10 digit key for RC2_40, 16 digit key for RC2_64 and 32 digit key for RC2_128.
- Allow Padding to Key: Choose yes to allow padding to the key to make exactly the value required for the mentioned algorithm.
Encryption during Message Flow
Payload encryption refers to encryption of whole or part of data that is transmitted in an event process on routes.
Encryption Key Configuration
Encrypt/Decrypt feature is used for security purpose to encrypt the data in output response generated from components so that the sensitive data will be more secure from normal users. Encrypted data in a flow can be decrypted after receiving the encrypted data at the component's input port as per the details in the Encrypt/Decrypt configuration page. The steps involved in enabling the encrypt/decrypt feature has been described as below:
Adding KeyStore Configuration
- In eStudio, open Configuration Repository panel (Window > Show View > Other > Fiorano), right-click on Resource and select Add Configuration option to open the dialog box for adding new Resource Configuration.
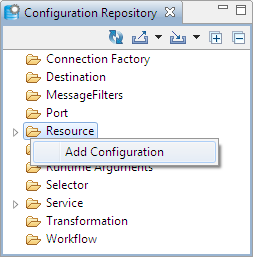
Figure 2: Navigating to add keystore configuration - Select the Resource Type as "Keystore" and click Next.
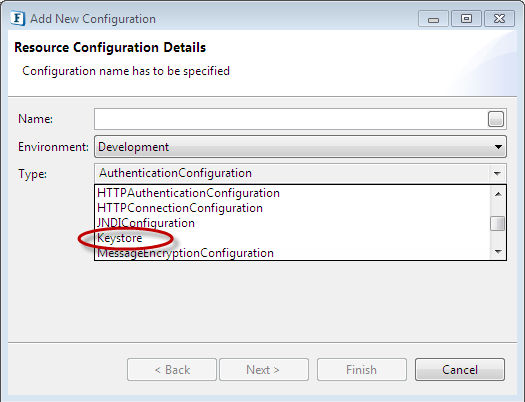
Figure 3: Choosing Keystore Resource Type in Resource Configuration Window - Click on Next and provide any String of your choice (recommended minimum of 6 characters for better security) and click Finish to save the keystore which will be used as the key for encryption/decryption of data.
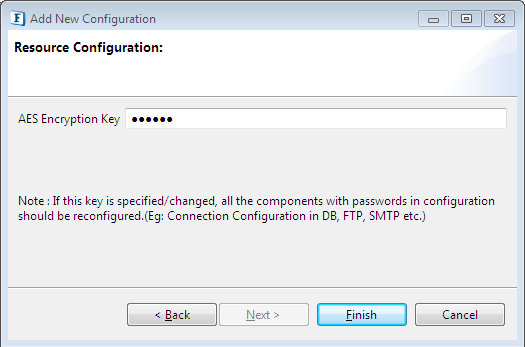
Figure 4: Adding Encryption Key
Configuration in Component
Encryption/Decryption feature is available in all of the components. Depending on the type of functionality, some components support only encryption of the output response data while some components support only decryption of the data received at its input port and some support both. For example, POP3 supports only encryption feature, SMTP supports only decryption while Feeder supports both functionalities.
A sample flow explaining the encryption/decryption feature can be done using SMTP/POP3 components in which POP3 is used for encryption of email data received from the mail server while SMTP is used to decrypt the encrypted data received from POP3 to send mail to the required recipients as per the email data.
- Open POP3 CPS and enter the details of the mail server from which the emails are to be fetched and go to the Interaction Configurations panel. Select Show Expert properties and click the Select Elements to Encrypt ellipsis button to open the encryption configuration editor.
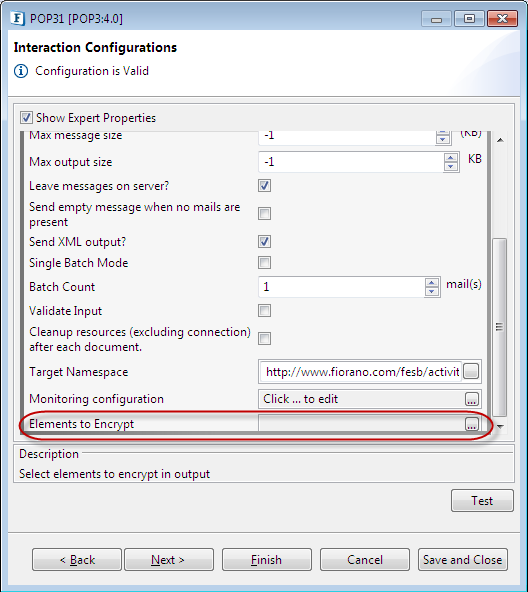
Figure 5: Elements to Encrypt property
- Select the elements for which the data has to be encrypted from the structure available on the top left of the page and click on the small right arrow to add the selected elements to the list on the top right. Here, we selected "To" field in the Email data so that it will be encrypted in the output response from POP3.
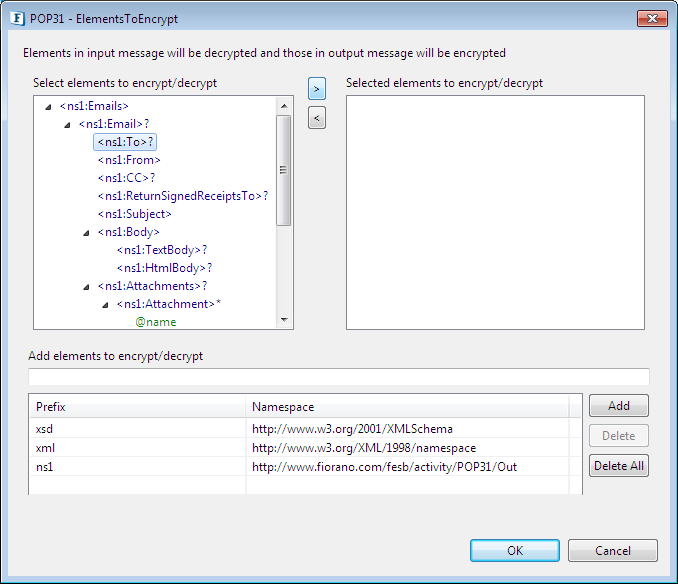
Figure 6: Encrypt/Decrypt Configuration page in POP3
- If any of the elements which are to be encrypted are not available in the structure tree shown, user can add the corresponding elements Xpath in the Add elements to encrypt/decrypt textfield. All the extra elements added in the text field will also be encrypted along with the selected elements from the structure.
- If any of the namespaces for the selected/newly-added elements are not already available in the namespaces list, the user needs to add the corresponding namespaces for proper identification of the element from the Xpath entered in the textfield.
- After completing the selection/addition of required elements to be encrypted from POP3, click OK to save the configuration and Finish the CPS after making any other POP3 configuration changes required for the flow.
- Next, open the CPS of SMTP and enter the details of the mail server which is used for sending emails and other common properties and proceed to the interaction configurations page. Select Show Expert properties and click on Select Elements to Decrypt to open the Encrypt/Decrypt configuration editor in SMTP.
- Select the elements from the structure tree on left for whom the input data has been encrypted and needs decryption before processing the message. As we selected the "To" element in POP3 for encryption, the same element needs to be selected here for decryption of the encrypted data sent from POP3.
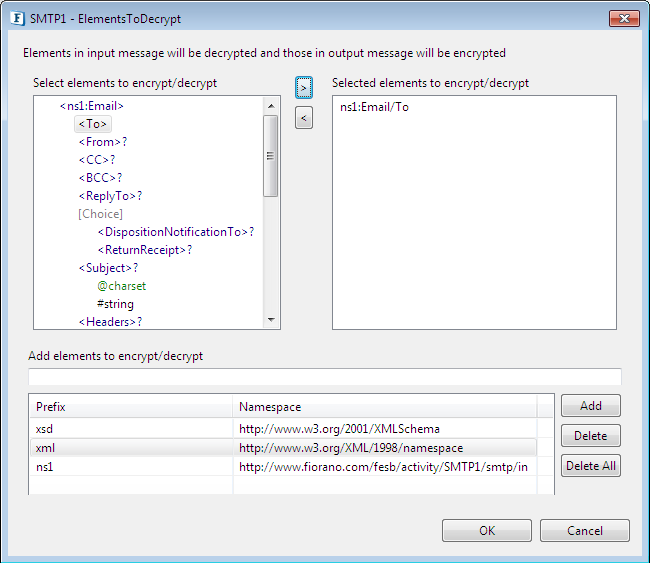
Figure 7: Encrypt/Decrypt Configuration page in SMTP
- Add any other extra elements in the Add elements to encrypt/decrypt textfield if the input data for them is encrypted and needs decryption, but the elements are not available from the structure tree. Once all the required elements have been added, click OK to save the configuration.
- Sample flow for POP3 and SMTP with encryption/decryption enabled would be as shown below:
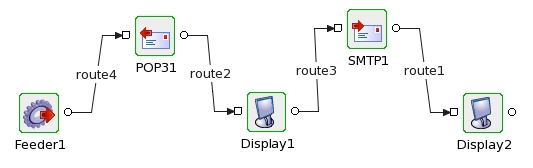
Figure 8: Sample Encrypt/Decrypt flow with POP3/SMTP
- After the event process has been launched, POP3 will start sending the emails it fetched from the mail account to its OUT_PORT. Since Encryption is enabled for the "To" element, the "To" field in the output response will be encrypted as shown in the figure below, which is the response we get on "Display1" from POP3. The encrypted output data from POP3 becomes the input for SMTP and decryption is done for the selected elements in Encrypt/Decrypt page before sending the processed data to the recipients in the email data.
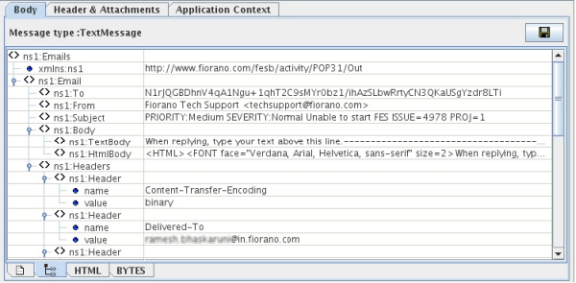
Figure 9: Output Response from POP3 on Display1 in which the "To" field is encrypted
Encryption/Decryption feature works the same way in all the components, apart from the ones with multiple ports in which there will be one Encrypt/Decrypt configuration for each of the input/output port available for the component. Components like WSStub, RESTStub, CBR etc. have this feature since they will be having multiple ports at a time in complex flows. The steps involved in the configuration for WSStub component has been explained below:
- In case of WSStub, Open the WSStub CPS, then load any WSDL with at least one operation and click Next till the Miscellaneous Configurations panel. Click the Encrypt/Decrypt Configuration tab on the top to open the required Encrypt/Decrypt configuration settings page.
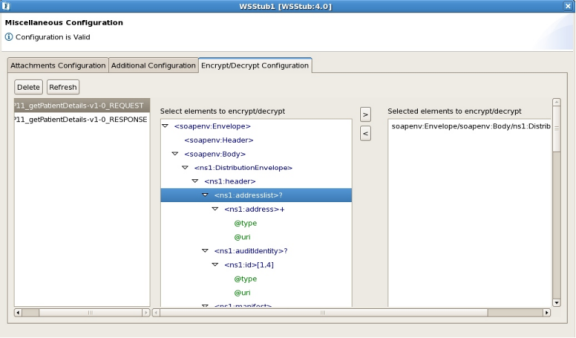
Figure 10: Encrypt/Decrypt Configuration Page in WSStub with Single Operation
- On the left side of the page, click on the Refresh button to add all the available ports for the WSStub component to the list of ports. There will be two ports for each operation in WSStub, one for Request and one for Response of the operation. Select any of the Request/Response port to load the encrypt/decrypt configuration panel for that port in the window to the right.
- Once any of the port has been selected, selecting elements for Encryption/Decryption will be in the same way as explained above for the POP3/SMTP event process, the only difference would be to configure separate encryption/decryption configuration for each of the ports available individually. After the completion of selecting the elements for Encryption in case of Response Port (or Decryption in case of Request Port), click on Finish to save the configuration and the component is ready to launch with encryption/decryption enabled for the output/input data.