XMLSecurityProvider is used for encrypting and signing the XML data.
The Configuration Property sheet (CPS) provides an option to choose elements for encryption/decryption.
Configuration and Testing
Interaction Configuration
The component has the following attributes which can be configured from the CPS (Configuration Property Sheet) below.
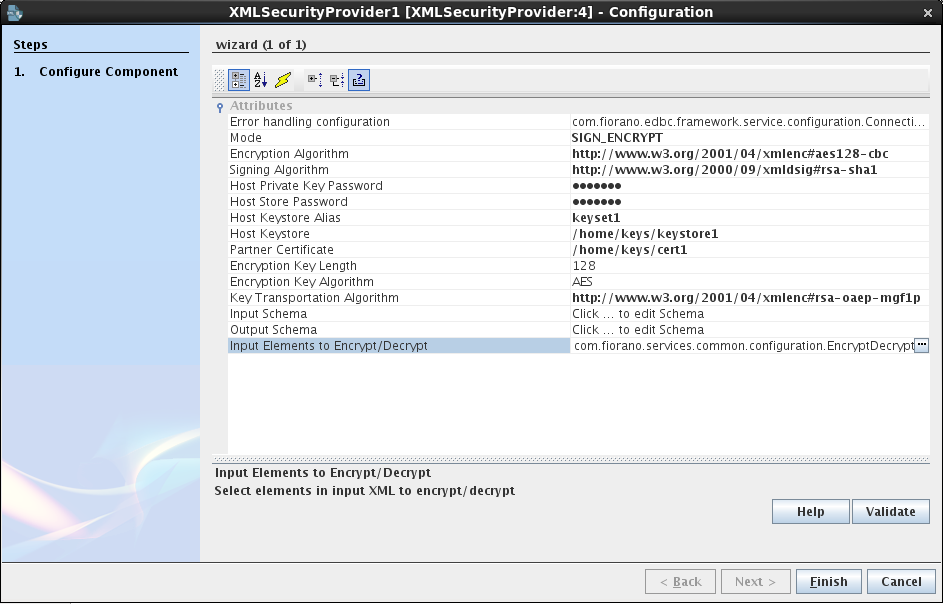
Figure 1: Configurable properties of XMLSecurityProvider component
Mode
Operations available in the component. The modes available are described in the table below.
| Mode | Description |
|---|---|
| ENCRYPT | Used to encrypt the data with given credentials using host certificate. |
| DECRYPT | Used to decrypt the selected elements by the hosts private key. |
| SIGN | Creates signature using private key. |
| VERIFY | Used to verify the authenticity of the received message. |
| SIGN_ENCRYPT | Encrypts the data and produces the signature. |
| VERIFY | Verifies if the signature is received from the authenticated source. If the file does not come from the expected source, that is, if the signature does not match or if it is tampered, an error gets logged. |
| DECRYPT_VERIFY | Decrypts the data and verifies the signature received. |
Encryption Algorithm
Algorithm to be used for encrypting data.
Signing Algorithm
Algorithm to be used for Signing the data.
Host Private Key Password
Password for the private key.
Host Store Password
Password for the keystore used.
Host KeyStore Alias
Alias name given for the keypair entry in the keystore.
Host KeyStore
Keystore path which contains KeyPair.
Partner Certificate
PartnerCertificate path representing the alias.
Encryption Key Length
Length of the encryption key to be generated.
Encryption Key Algorithm
The private key is encrypted once again to strengthen the security measures.This is the algorithm which is to be used for encrypting the private key.
Key Transportation Algorithm
Transport Algorithm takes a different approach that provides higher security assurance, by encrypting a random integer with the recipient's public key, and using a symmetric key-wrapping scheme to encrypt the keying data.
Input Schema
Schema used for generating XML data.
Output Schema
Schema for the output message.
Input Elements to Encrypt/Decrypt
Drag and drop the elements from the generated XML structure.These elements will be used for encryption and signing.
Functional Demonstration
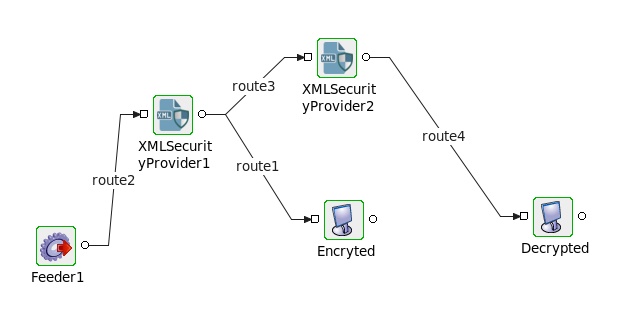
In the flow shown in the figure below, XMLSecurityProvider1 is configured with SIGN_ENCRYPT and XMLSecurityProvider2 is configured with DECRYPT_VERIFY. The Input XML is fed-in using the Feeder component. Display components are connected in such a way that the encrypted data from XMLSecurityProvider1 gets displayed in Encrypted display component and decrypted data from XMLSecurityProvider2 gets displayed in Decrypted display component.
Title element is selected for encryption in the following scenario.
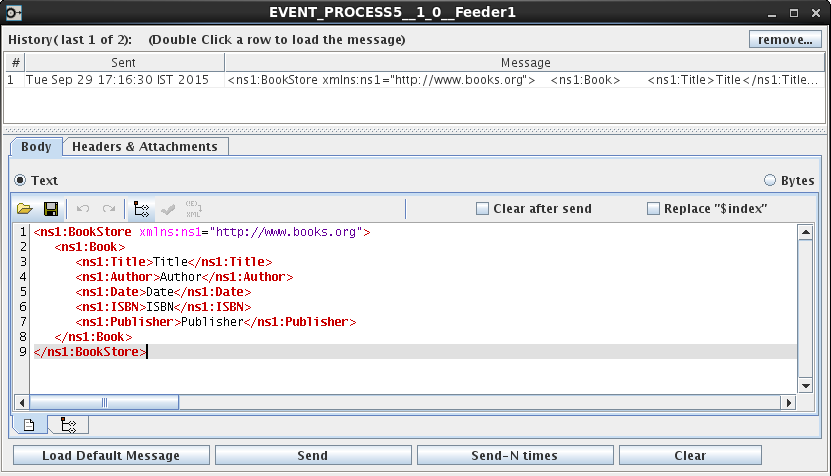
Input
Below is the Input XML.
Output
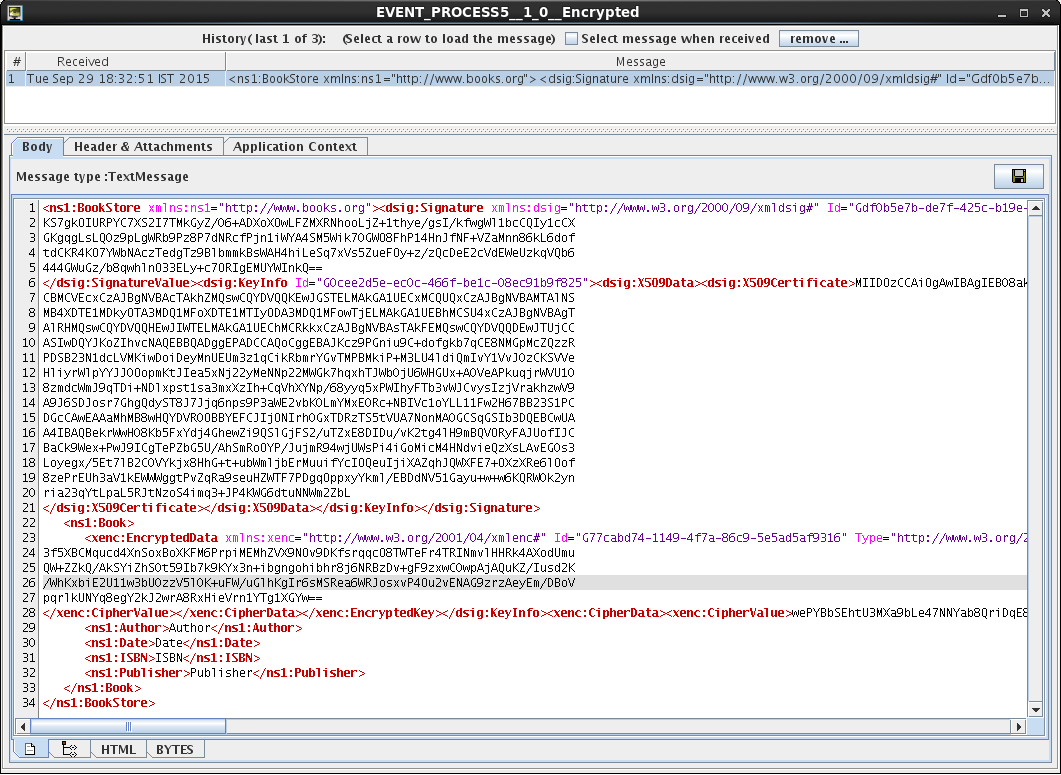
Encrypted Output
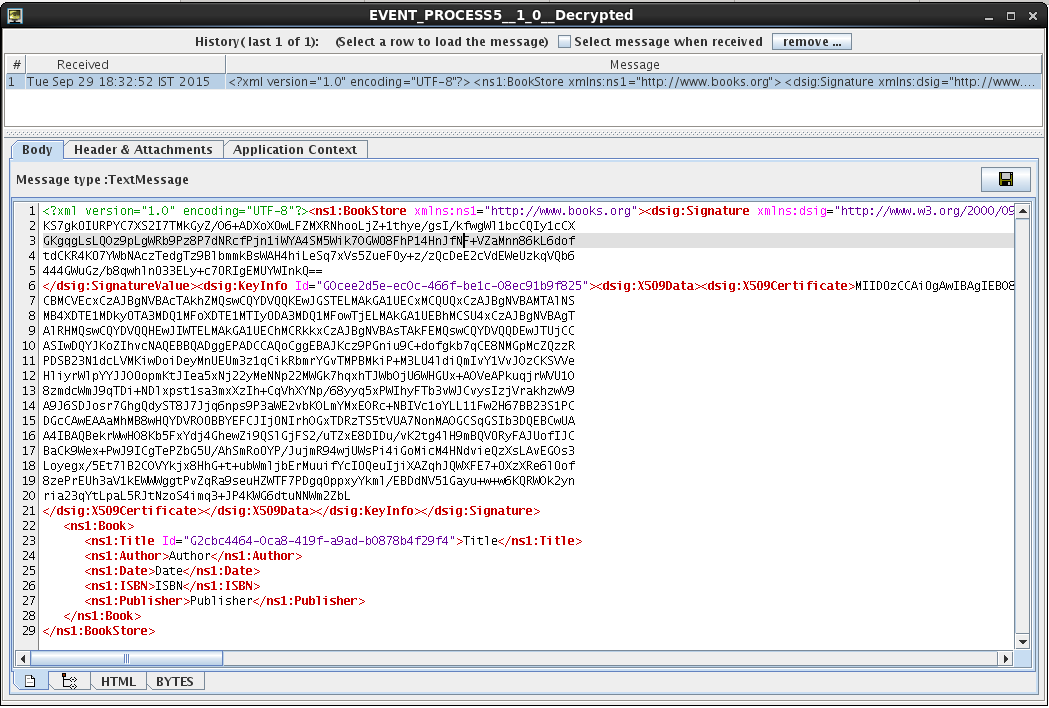
The encrypted output for the input XML provided is as shown in the figure below.
Notice that dsig:Signature tag consists of algorithm digest data and all the algorithms used for operations. These would be collected by the receiver to extract the digest and verify the things. Title is encrypted as it was selected for encryption.
Decrypted Output
The final Decrypted and verified (successful) output is displayed in the Decrypted display. The value of Title gets retrieved back.