This policy protects API from any possible XML Threats by setting limits to various attributes present in the XML structure.
Configuration
The properties that have to be configured to use the policy are described below.
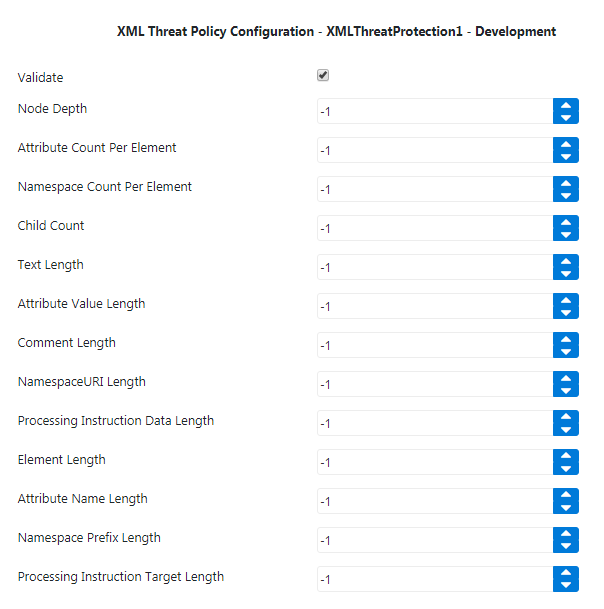
Figure 1: XML Threat Protection Policy Configuration attributes
| Property | Description |
| Node Depth | Maximum number of nodes allowed in the XML. |
| Attribute Count Per Element | Maximum number of attributes allowed within an element in the XML. The attribute “category” is checked for the specified limit. |
| Namespace Count Per Element | Maximum number of characters allowed in a namespace within an element in the XML. |
| Child Count | Maximum number of child elements allowed per element in the XML document. |
| Text length | Character limit for text nodes present in the XML document. |
| Attribute Value Length | Character limit for attribute values present in the XML document. |
| Comment Length | Character limit for comments present in the XML document. |
| Namespaceuri Length | Maximum number of characters allowed in a namespace URI within an element in the XML file. |
| Processing Instruction Data Length | Maximum number of characters for the Processing Instruction Text present in the XML file. ( A Pocessing Instruction starts with a special tag <? and ends with ?> ) Example: <?xml-stylesheet href = "/style.xsl“ type = "text/xsl"?> Here, length of type and href values are checked. |
| Element Length | Maximum number of characters allowed in an element name in the XML file. |
| Attribute Name Length | Maximum number of characters allowed in an attribute name in the XML file. |
| Namespace Prefix Length | Maximum number of characters allowed in a Namespace Prefix within an element in the XML file. |
| Processing Instruction Target Length | Maximum number of characters for the target of any processing instruction text present in the XML file. Example: <?xml-stylesheet href = "tpstyle.css" type = "text/css"?> |
Examples
Below are a couple of examples illustrating sample configurations.
Example 1
Configure XML Threat policy with the values shown in the below figure and set it to the scope 'Target Response'.
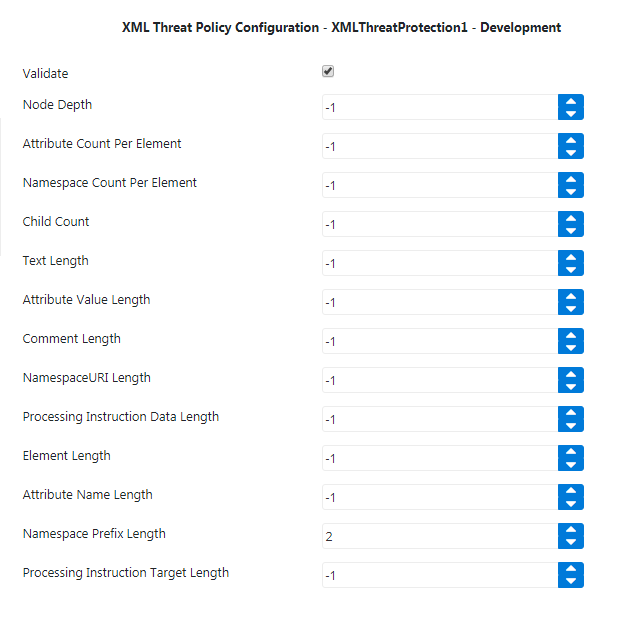
Figure 2: XML Threat policy properties with values provided in Example 1
In the above figure, Namespace Prefix Length property is set to ‘2’.
Below is the output when a request is processed without XML Threat Policy.
When the request is sent after setting XML Threat Policy, the error below is displayed as namespace prefix length is beyond the set value ‘2’.
|
Example 2
Edit the configured XML Threat policy and set the Node Depth to ‘3’.
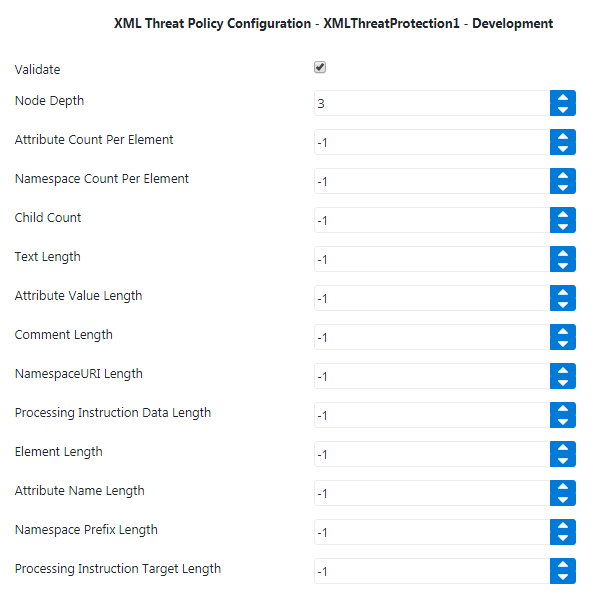
Figure 3: XML Threat policy properties with values provided in Example 2
Below is the output when a request is processed without XML Threat Policy:
When the request is sent after setting XML Threat Policy, the error below is displayed as the node depth is beyond the set value 3.
|
