Following sections illustrate how to use an LDAP policy.
Adding LDAP Resource
In-order to use the LDAP Policy, first create LDAP Resource to configure LDAP Server connection details.
Perform the following actions to create an LDAP Resource:
- In the API Dashboard, click Administration Options For API Manager (Admin) prompt.
- Click the LDAP Resource Tab.
- Add an LDAP Resource using the Add
 button.
button.
Configure the properties as described in LDAP Resource section, after which it can be used while configuring the the LDAP Policy as below.
Configuring based on the LDAP Policy Types
Add the LDAP policy by selecting LDAP option in the Security tab.
LDAP Policy basically has three configurable Policy types which represent different functionalities:
Authentication: User Name and Password Authentication
Search and Authenticate: DN (Digital Number) Attribute Authentication
Search: Searching LDAP
The following sections discuss about each one in detail.
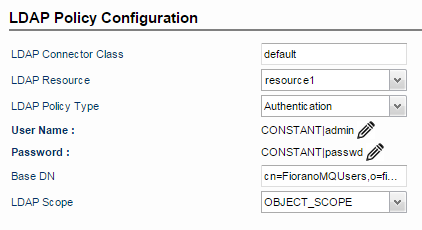
Authentication (User Name and Password Authentication)
This provides authentication against an LDAP provider. The policy passes username and password from the request to LDAP for authentication.
Provide the property values following the descriptions in the LDAP section.
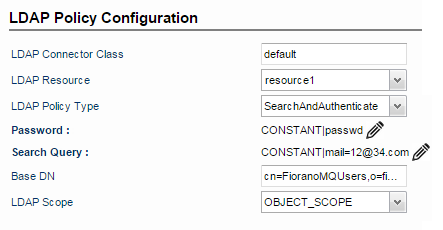
Search and Authenticate (DN Attribute Authentication)
If username is in the request, whereas you want to authenticate a user with a DN attribute other than username, such as email, include a Search Query to get the user email associated with the password. The LDAP policy uses email address to query the LDAP provider for the corresponding user name, which is then used for authentication.
Search (Searching LDAP)
By identifying the user with metadata in the request or response, you can use this element to retrieve additional DN attributes for the user from LDAP. For example, if the request contains the user email, and your LDAP defines a "mail" attribute for storing user email addresses, the query searches LDAP for an email matching the email in the request, and the policy can now retrieve additional DN attributes for that user with the Attributes element.
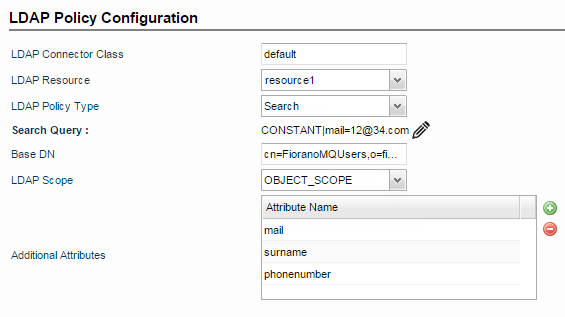
Additional Attributes
Attributes that need to retrieved. Use one or more attributes to identify the DN metadata you want to retrieve for the user. At least one attribute is required. For example, after the Search Query identifies the user, the policy can now retrieve DN attributes for the user such as address, phone number, and the user's title.
Attribute values are the DN attribute names defined in your LDAP.
After retrieving the attribute values from LDAP, these values will be stored in the context variables as below.
The flexible format of this variable—the "index" in particular—accounts for multiple attributes, as well as attributes with multiple values. Index is a number that starts at 0.
If you wanted to retrieve the third address attribute in the search results, you could use the following:
If an attribute had multiple values (for example, if a user has multiple email addresses), you could retrieve the second email address from the results in the following manner:
Using a custom LDAP provider
A default LDAP provider is already configured to interact with the LDAP Policy.However, if you are using a custom LDAP provider, enable the provider to support the LDAP Policy by performing the following actions:
In your LDAP provider class, implement the LDAPConnectionProvider interface.
- Create a Jar with your implementation classes and add it to the server.conf file under <java.classpath> section. This will add the jar to the class path.
- In the <LDAP Connector Class> of the policy configuration, add the fully qualified class name of your custom LDAP provider.