...
- Click the Events tab from the Navigation Panel and choose Latest option; a list of latest Events generated by FES and FPS is displayed.
- Click the Filter Events button , as shown in the figure belowpresent at the upper-right part of the screen; the Set Event Filters dialog box appears (Figure 10).

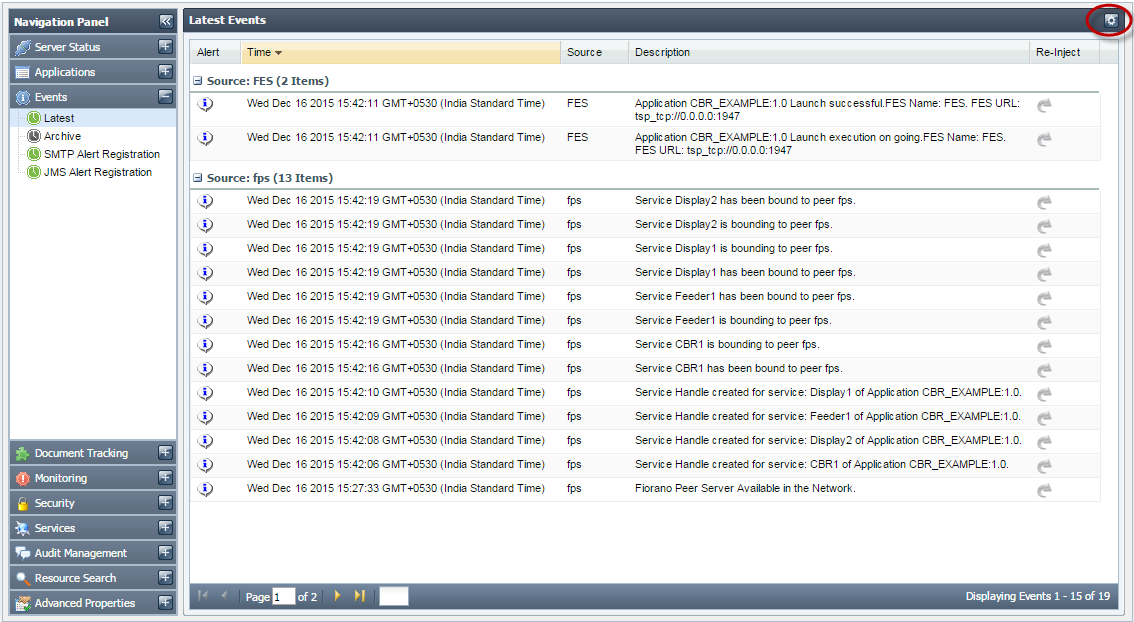
Figure 9 : Filter Events Button
Choose the Event Type and Event Category from the drop-down list and click Done.
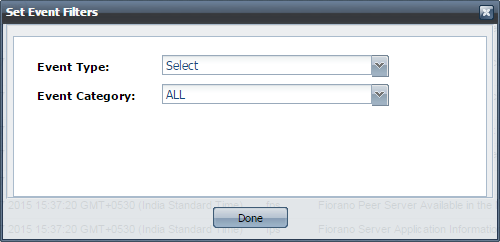
Figure 10: Set Events Filters dialog boxInfo More drop-down options appear as required depending on the Event Type and Event Category.
...
- Click the Events tab from the Navigation Panel and choose Archives option; a list of Archived Events is displayed.
- Click the Filter Events button, as shown in figure 11; the button present at the upper-right part of the screen; the Set Event Filters dialog box appears (Figure 12).

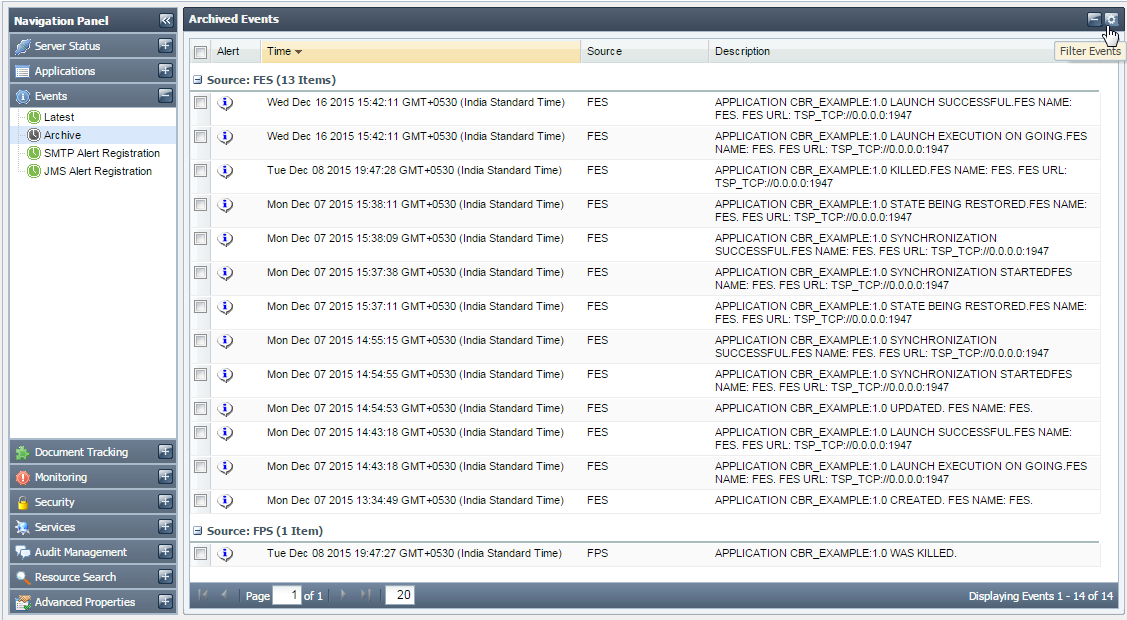
Figure 11: Filter Events button
- Choose Event Type and Event Category from the drop-down list and click the Search button, as shown in the figure below. The result appears on the screen.

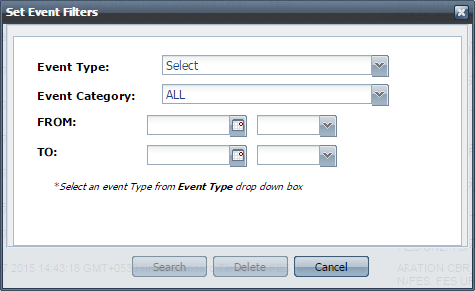
Figure 12: Set Event Filters dialog box
...
- Click the Events tab from the Navigation panel and choose the Archives option; a list of archived events appears.
- Select the relevant event and click the Delete selected records button present next to the Filter Events button.

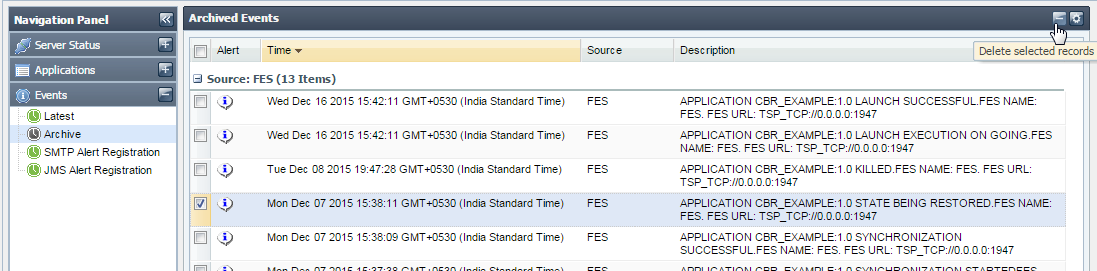
Figure 13: Delete selected records button
- The Events Table Updated dialog box appears confirming the deletion; click OK.

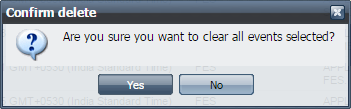
Figure 14: Event Table Updated dialog box
| Anchor | ||||
|---|---|---|---|---|
|
You can change the configuration of the mail server settings by going to the Configure SMTP Server Settings button. This page also provides an option to specify usernames and passwords in case the mail server requires authentication of these in order to send e-mails.
To add an Alert Configuration, perform the following:
- Click the Events tab form from the Navigation Panel and choose the SMTP Alert Registration option.
- Click the Add an Alert Configuration button; Configure SMTP Alert dialog box appears, as shown in Figure 16.

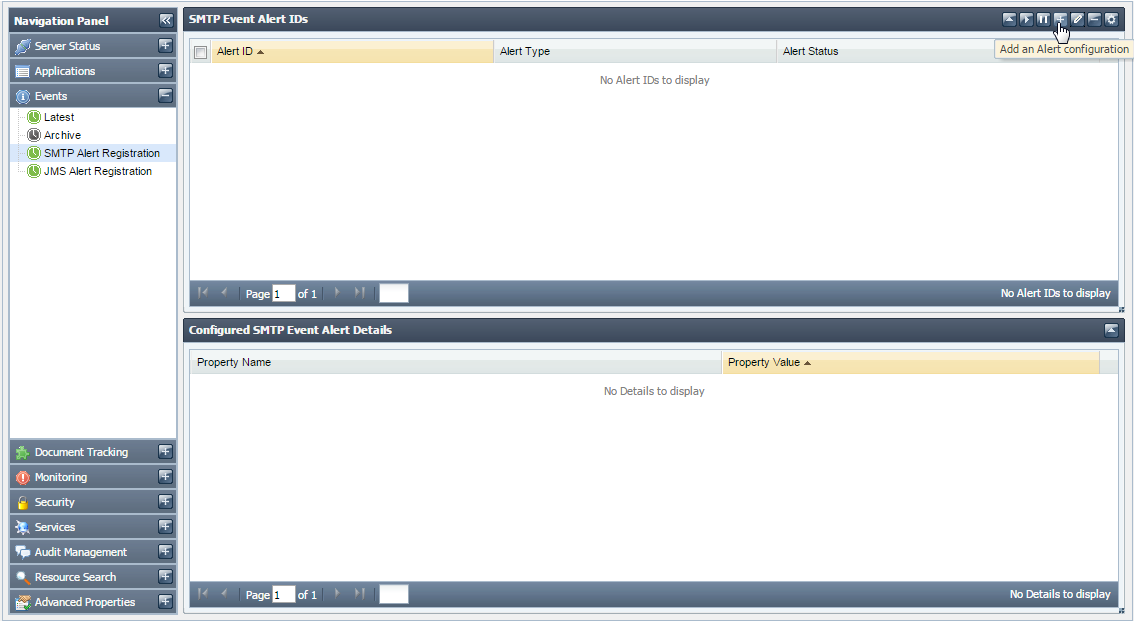
Figure 15: Add an Alert Configuration button
Choose the Event Type and Event Category from the drop-down list and enter the email ID of the recipient in Recipient Address field.
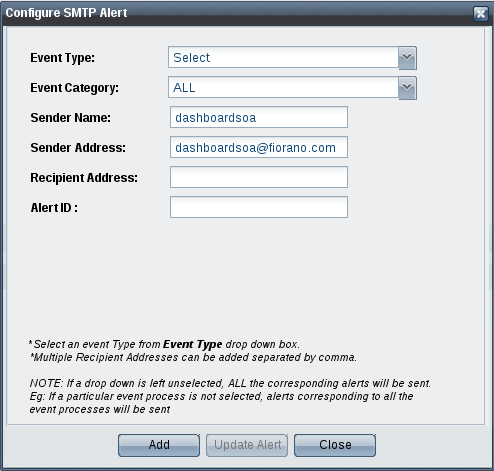
Figure 16: Configure SMTP Alert dialog box
Tip title List of Events Refer the List of Events section to see the list of events under each Event Type.
- Finally, click the Add button to apply the changes. The list of currently configured email alerts appears.

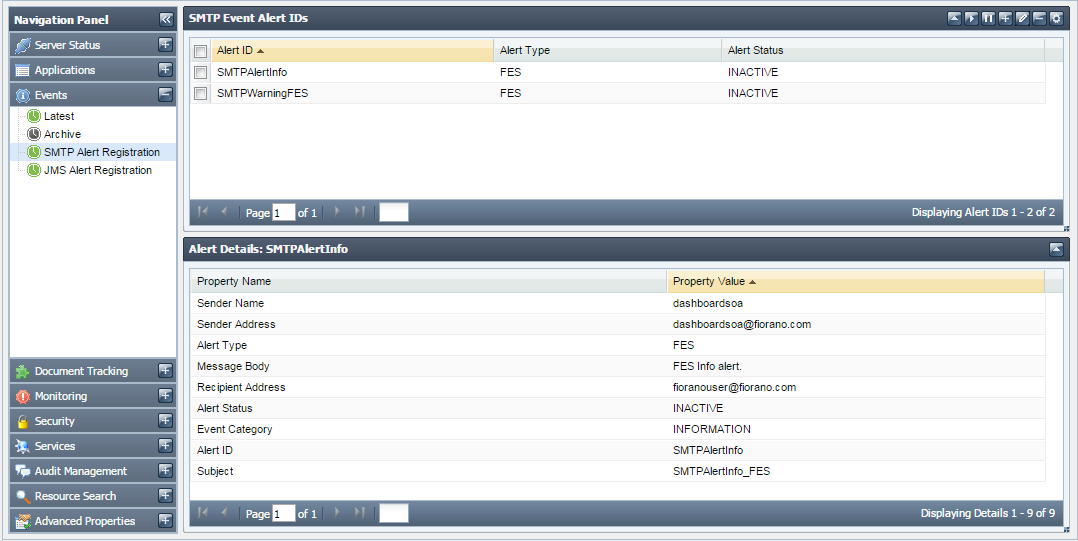
Figure 17: Event e-mail registration option
To configure SMTP server settings, perform the following:
- Click the Events tab form from the Navigation Panel and choose the SMTP Alert Registration option.
- Click the Configure SMTP Server Settings button; Configure SMTP Server Settings dialog box appears as shown in Figure 18.
- Enter the details and click on Validate button, if the validation is successful, then click SaveConfigurations button to save the configurations and click Done.

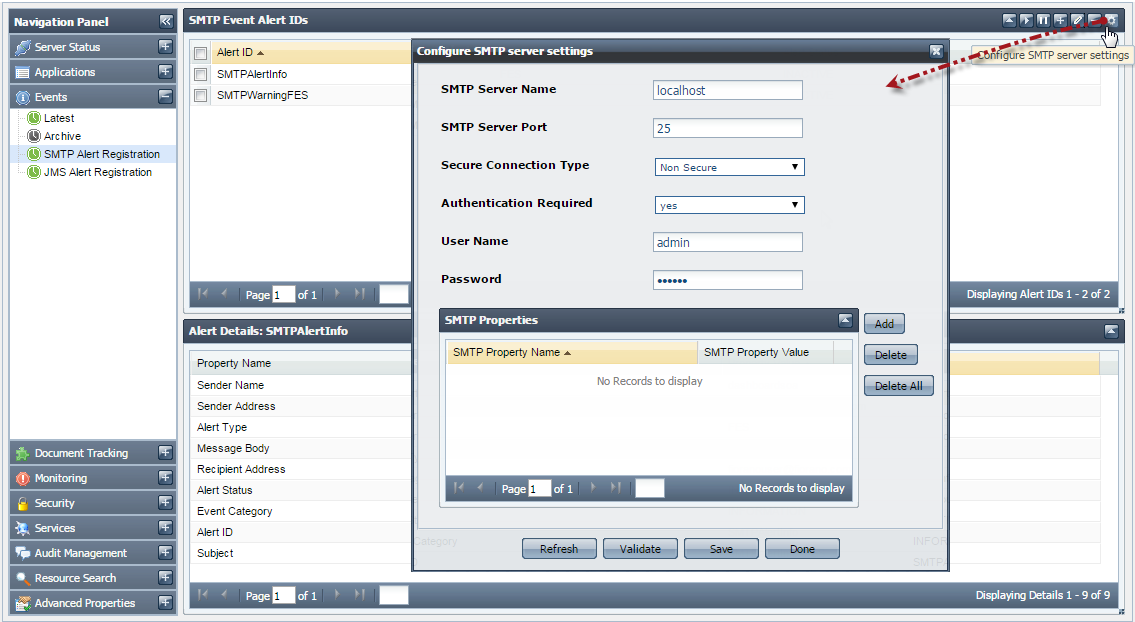
Figure 18: Configure SMTP Server Settings dialog box
...
To add an Alert Configuration, perform the following steps:
- Click the Events tab form from the Navigation Panel and choose JMS Alert Registration option.
- Click the Add an Alert Configuration button; Configure JMS Alert dialog box appears, as shown in Figure 20.

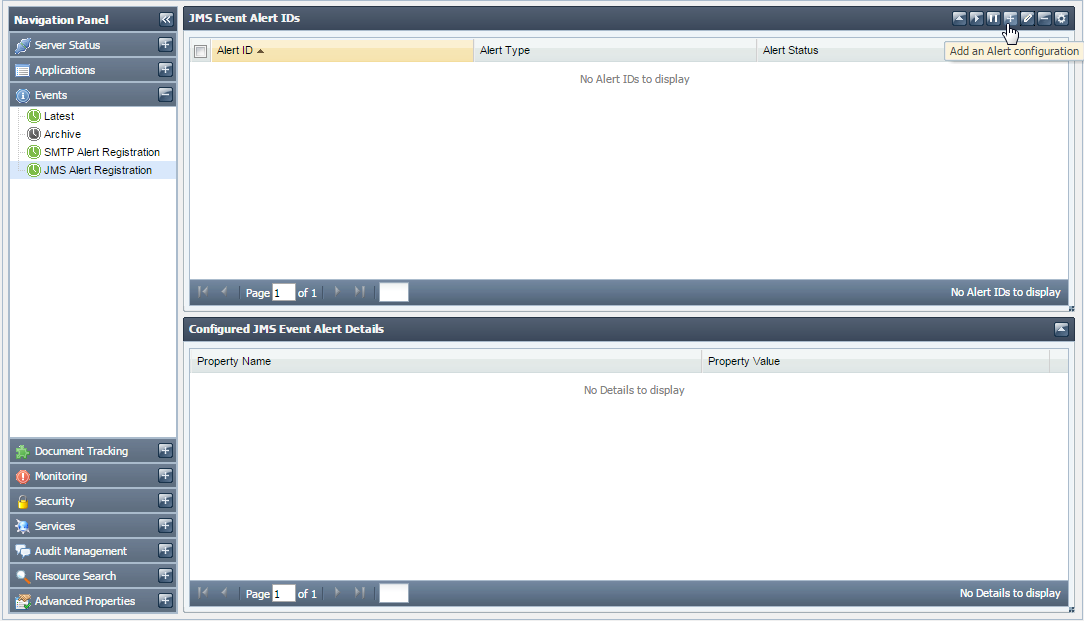
Figure 19: Add an Alert Configuration button
Choose the Event Type and Event Category from the drop-down list and enter the Destination Name(can be new or existing destination).
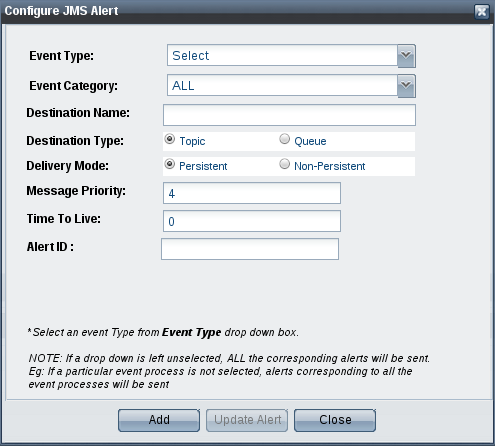
Figure 20: Configure JMS Alert dialog boxTip title List of Events Refer the List of Events section to see the list of events under each Event Type.
- Finally, click the Add button to apply the changes. The list of JMS configured alerts appears.

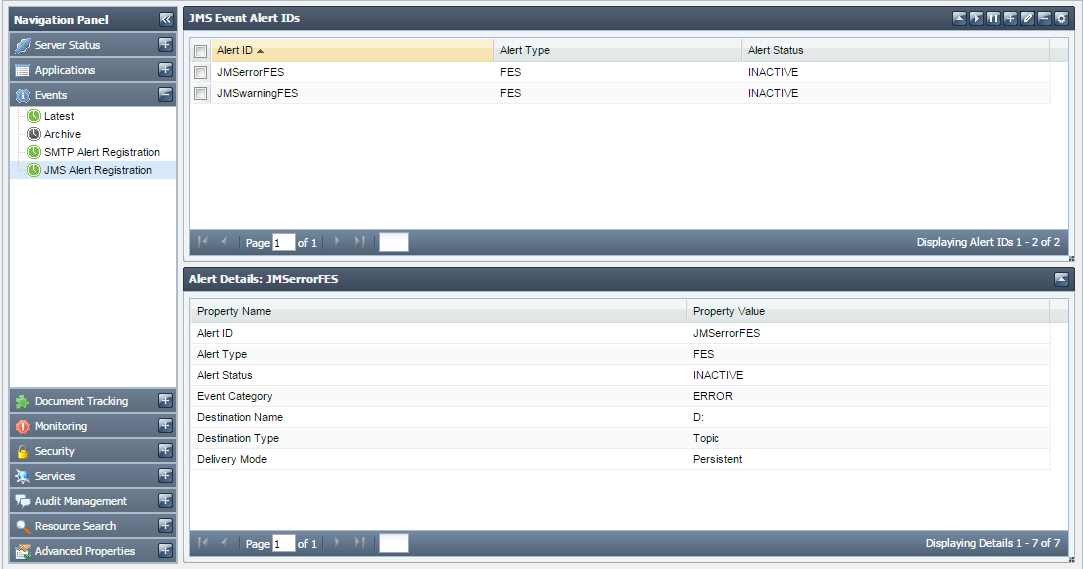
Figure 21: Event JMS registration option
To configure JMS Server settings, perform the following steps:per
- Click the Events tab form from the Navigation Panel and choose the JMS Alert Registration option.
- Click the ConfigureJMSServerSettings button; Configure JMS Server Settings dialog box appears, as shown in Figure 22.
- Enter the details and click the Validate button. If the Validation is Successful, then click Save Configurations button to save the configurations, and click Done.

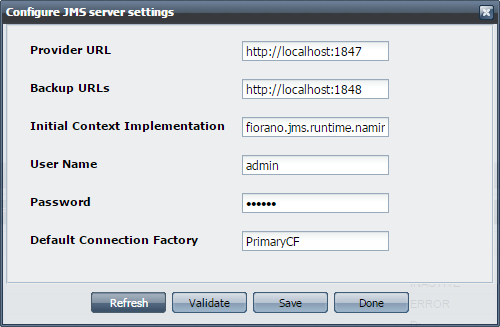
Figure 22: Configure JMS Server Settings dialog box
...
This section shows all the tracked documents in Fiorano Event Processes under SBW Workflows Count section along with details of the tracked documents under SBW Documents section below.
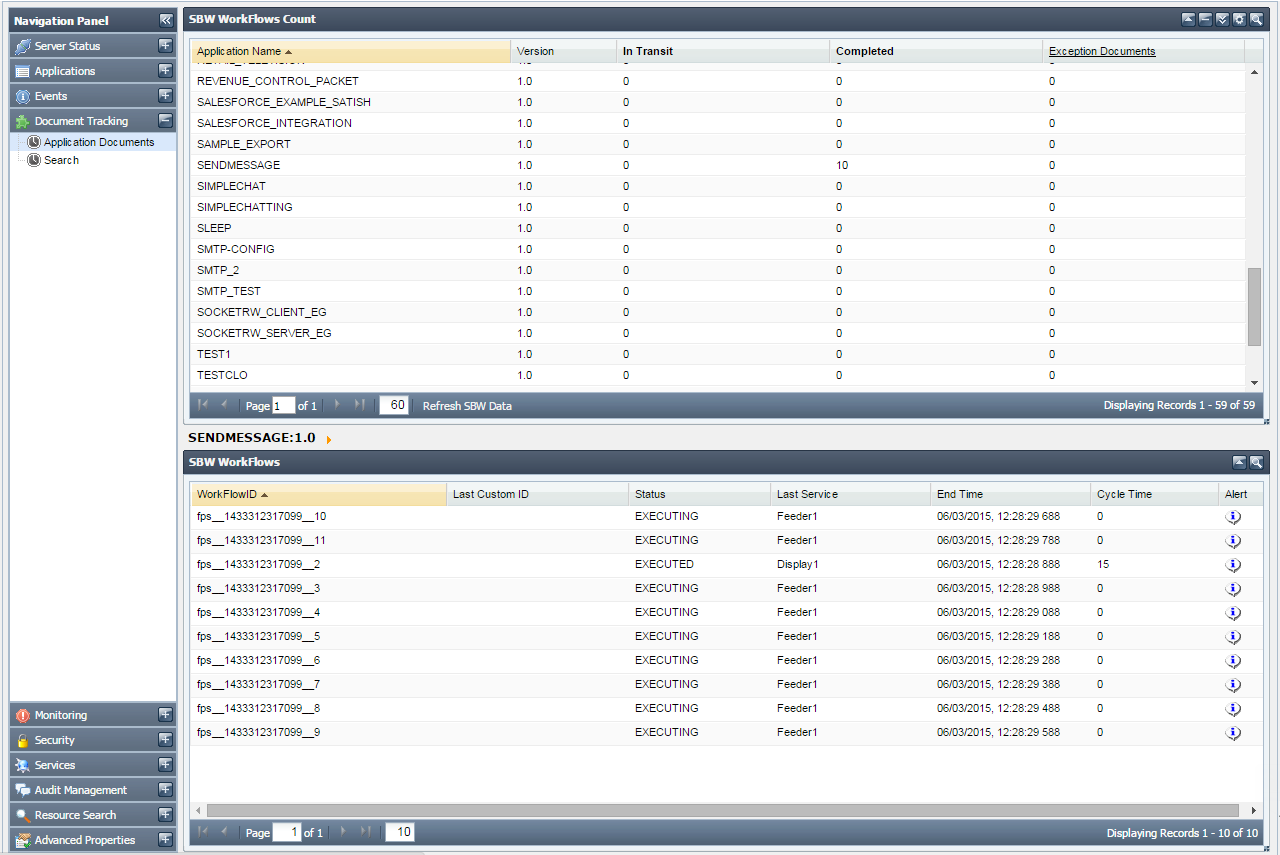
Figure 23: Document tracking tab showing tracked documents
The details of each tracked document can be seen by clicking the particular document's Workflow ID (see the figure above). This shows the document details such as the component processing it, time stamps, document IDs and the originating port of the tracked document.
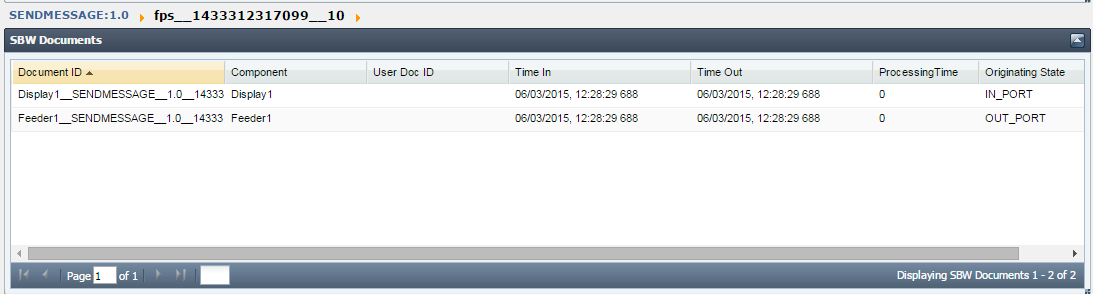
Figure 24: Details of the tracked document
Properties of the tracked documents can be seen by clicking on a particular Document ID (see the figure above), which shows the tracked document message properties, details of attachments, application context, message body and other general properties.
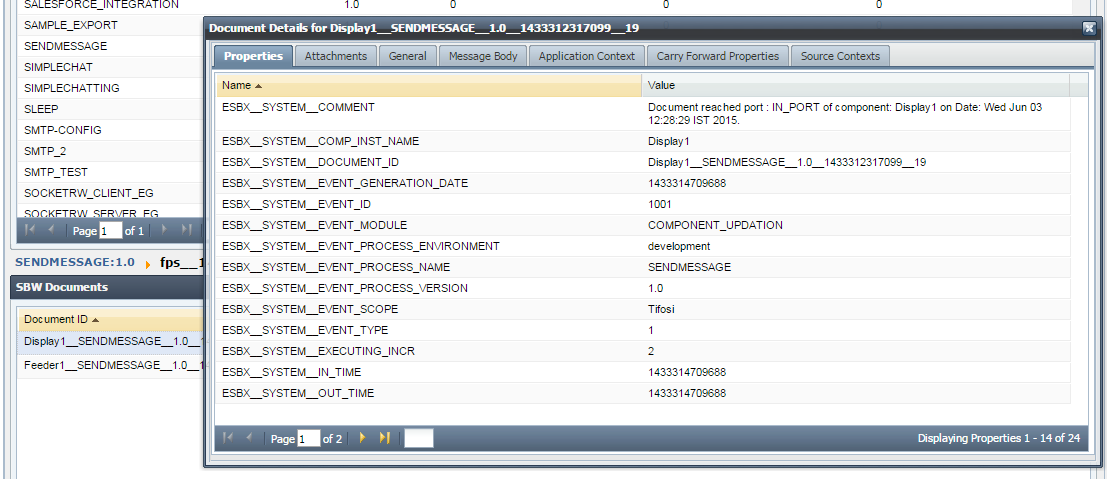
Figure 25: Tracked document
...
You can Enable/Disable Document Tracking at Application Level by clicking the Enable/Disable Application Level Document Tracking button present at the upper-right side of the screen. Select the Application and Version for which document tracking has to be enabled/disalbed and click Enable'/'Disable.
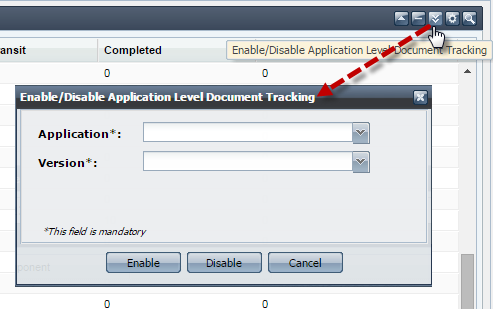
Figure 26: Application Level Document Tracking
...
You can reset the counters of Workflows and Exception Documents as visible in the Application Documents tab. The reset action can also be undone later. Click the Reset Counters button present at the upper-right side of the screen to to open Reset Counters dialog box. Select the Application and Version for which document tracking has to be reset and click Submit. The counters to be reset can be selected by selecting the appropriate checkbox, options being In Transit, Completed, Exception Documents and Undo Reset.
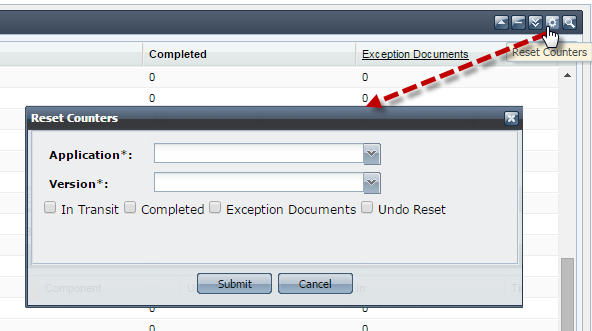
Figure 27: Reset Counters
...
The Dashboard supports searching of tracked documents based on various criteria such as, Application Name, Version, Service, Port Name, User DOC ID, Workflow Instance ID, Document ID, FPS Name, Status. Document Status (EXECUTED or EXECUTING) and Message. In addition, documents can be searched based on their date they were generated. To provide the search options, click Search section and then click the Filter SBW Documents button present at the upper-right part of the screen.
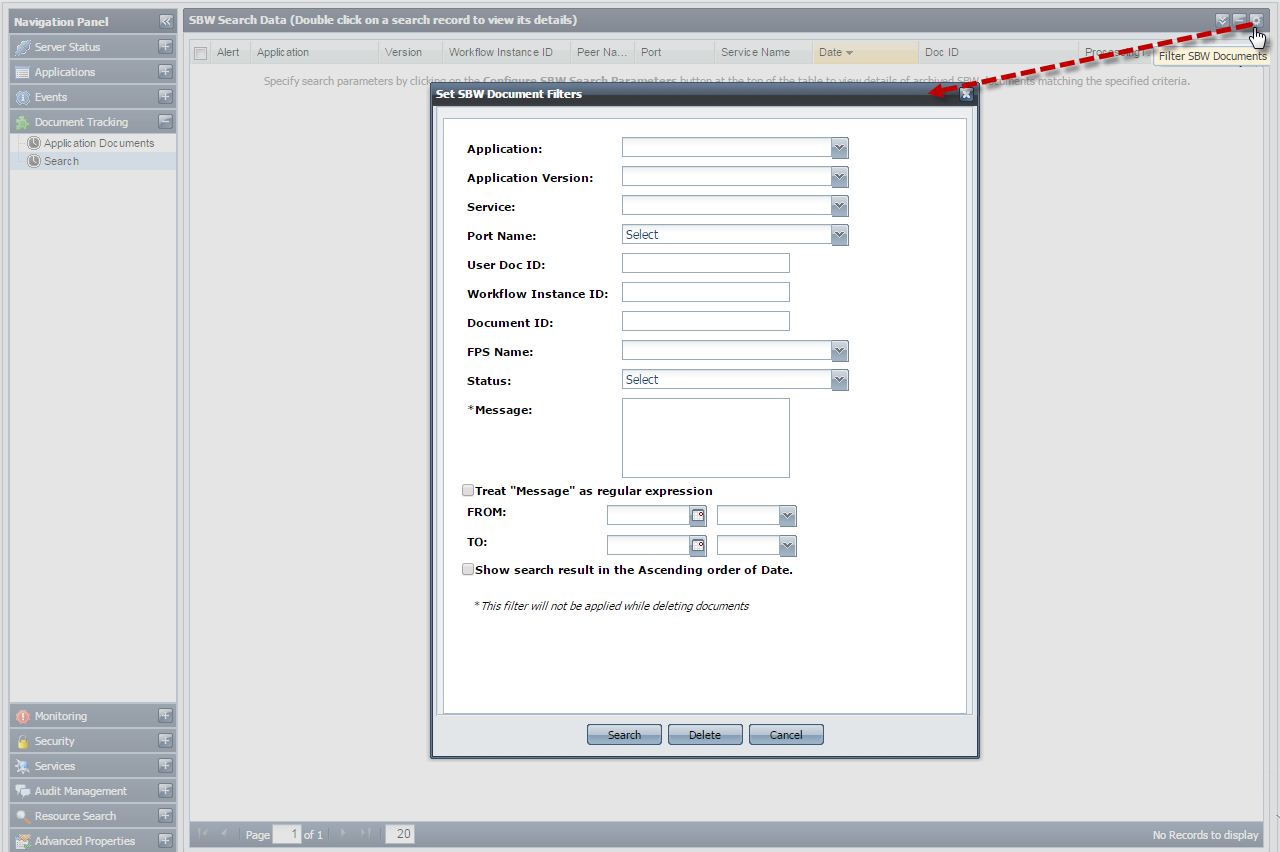
Figure 28: Searching tracked documents
...
| Tip |
|---|
Refer to the Re-injecting Failed Documents page to understand more about failed documents and re-injection. |
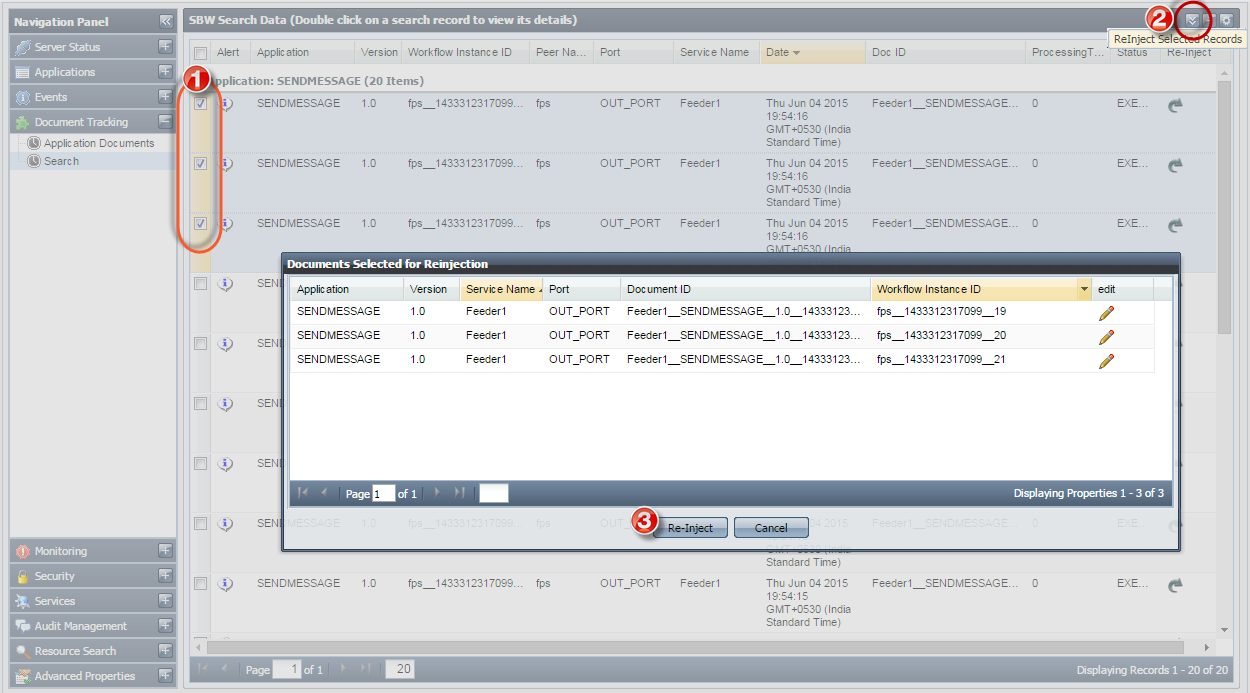
Figure 29: Selecting documents to reinject
...
To delete a document or a selected set of documents, select the record(s) and click Delete Selected Documents button present in the upper-right part of the screen.
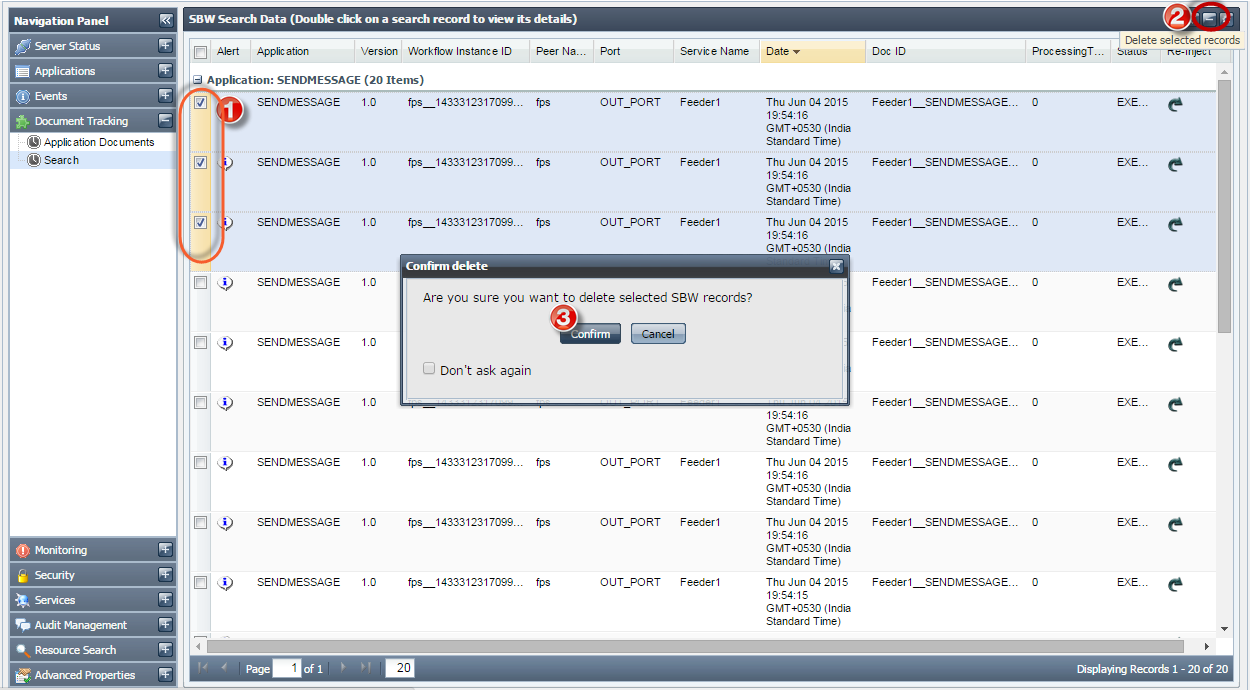
Figure 30: Selecting documents to delete SBW records
...
- Backlog Policy
- LowMemory Policy
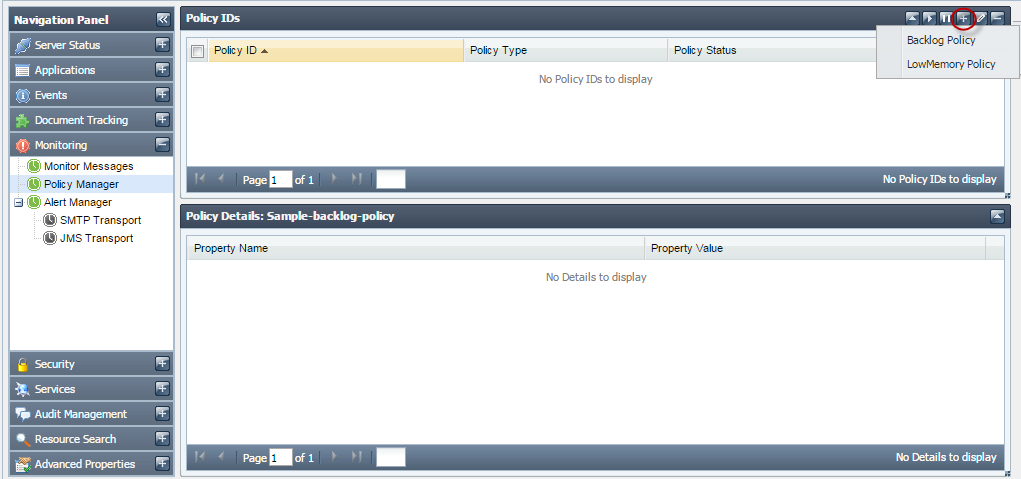
Figure 31: Policy Manager
...
Two types of alerts can be added:
- SMTP Alert
- JMS Alert
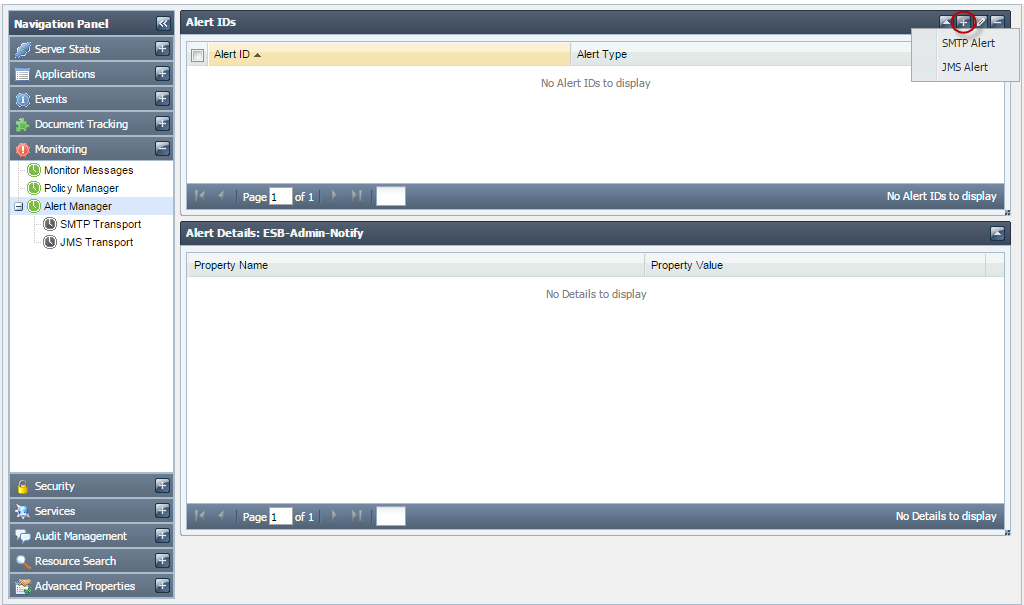
Figure 32: Alert Manager
This tab has two sub-tabs. These allow to specify the transport settings that will be used for sending the alerts. The settings can be specified for SMTP and JMS transports.

Figure 33: SMTP Transport

Figure 34: JMS Transport
...
Security section gives the security actions that can be performed in the Fiorano Network. These include adding/ editing users, groups, application level or group level permissions and validation or strength rules for passwords. These also include the principal store synchronization.formed in the Fiorano Network. These include adding/ editing users, groups, application level or group level permissions and validation or strength rules for passwords. These also include the principal store synchronization.formed in the Fiorano Network. These include adding/ editing users, groups, application level or group level permissions and validation or strength rules for passwords. These also include the principal store synchronization.formed in the Fiorano Network. These include adding/ editing users, groups, application level or group level permissions and validation or strength rules for passwords. These also include the principal store synchronization.
The Security tab has seven sections:
...
This tab shows you details of Users currently registered in the Fiorano network. The actions that can be undertaken in this tab include creating new users, deleting an existing user or changing password for an existing user, provided that you have the proper User Permissions to do so.
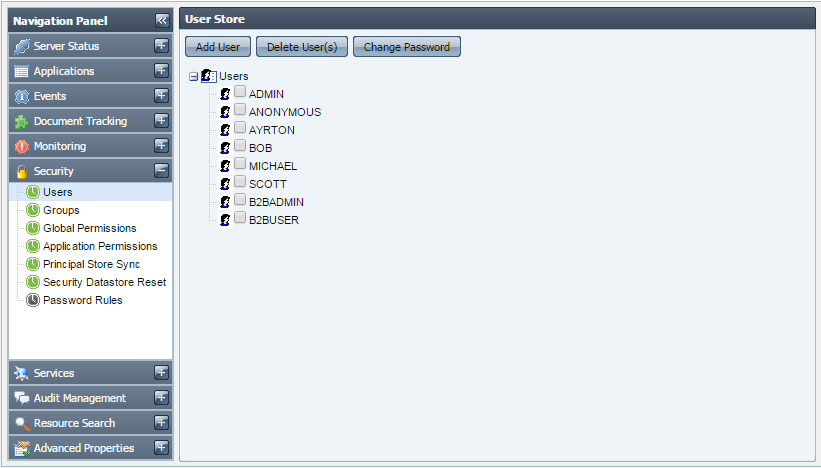
Figure 35: Users
...
This tab shows the groups registered in the Fiorano network. Groups allow grouping users together and applying actions on them together. The actions that can be undertaken in this tab include creating new groups, deleting/editing an existing group, provided that you have proper User Permissions to do so.
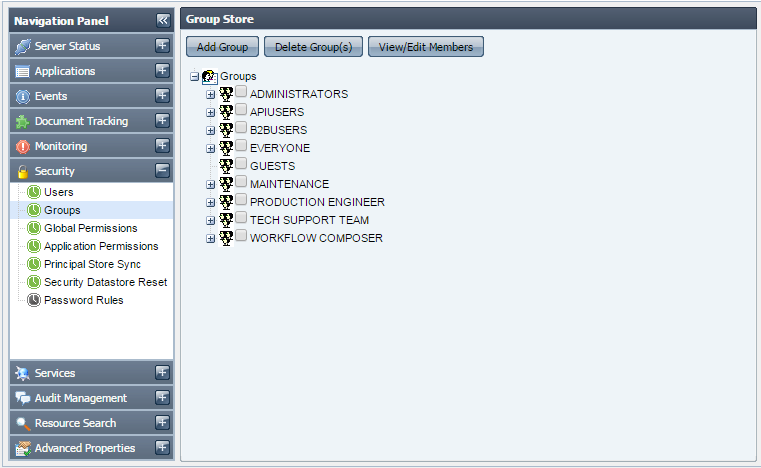
Figure 36: Groups
...
This tab shows the global permissions that are currently available in the Fiorano network. This tab allows you to edit or specify the users for whom these permissions will be applicable, provided that you have proper User Permissions to do so.
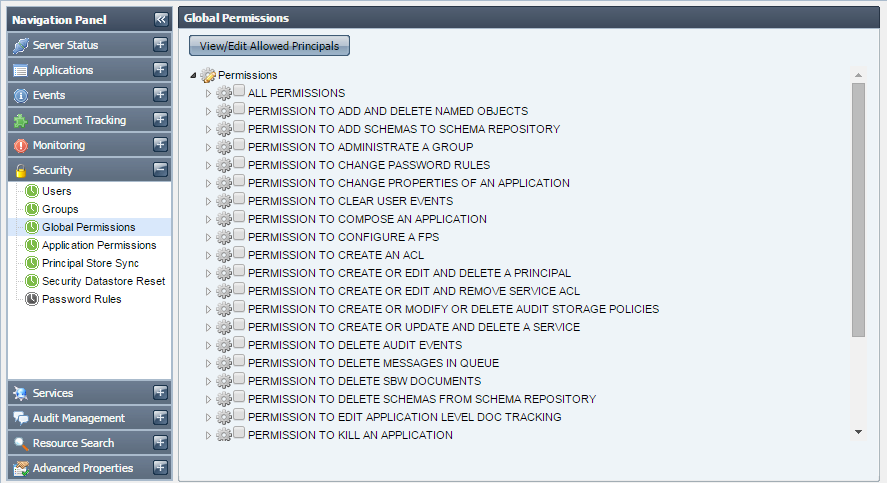
Figure 37: Global Permissions
...
| Info |
|---|
Application level permissions override global level permissions. For example, if a user is given launch permission for applications in global permissions, but for a particular application, he/she is not granted the permission to launch that application, then the user will not be allowed to launch that particular application. |
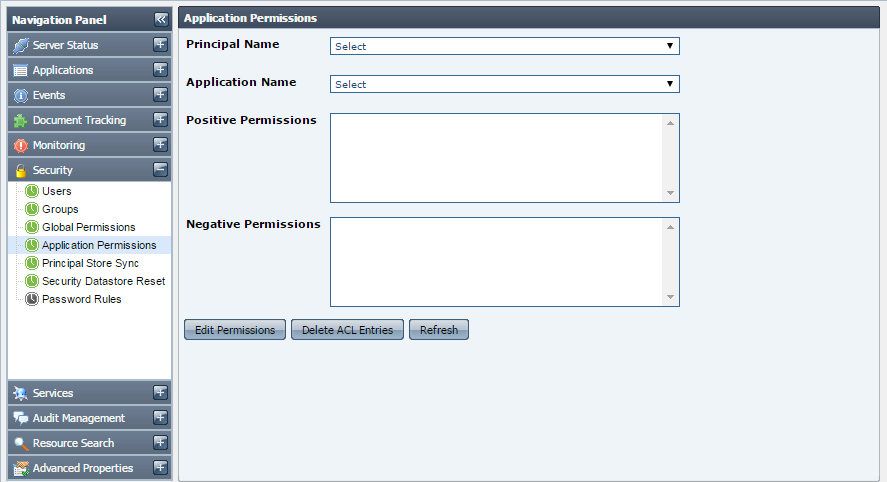
Figure 38: Application Permissions
...
This tab shows the principal store synchronization status for the connected peers. This also allows you to synchronize the store for a peer.
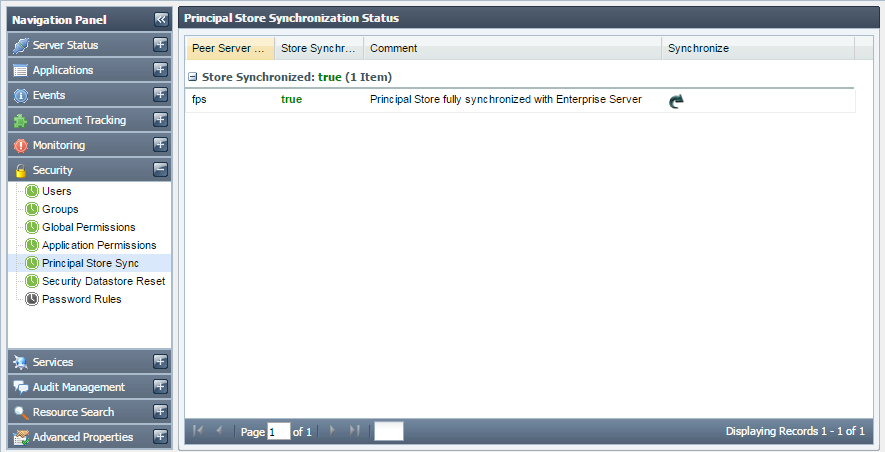
Figure 39: Principal Store Sync
...
This tab shows the Security Datastore of the Enterprise Network. It also allows the authorized user to reset the entire Security Datastore viz. the Principals and the ACLs to system default.
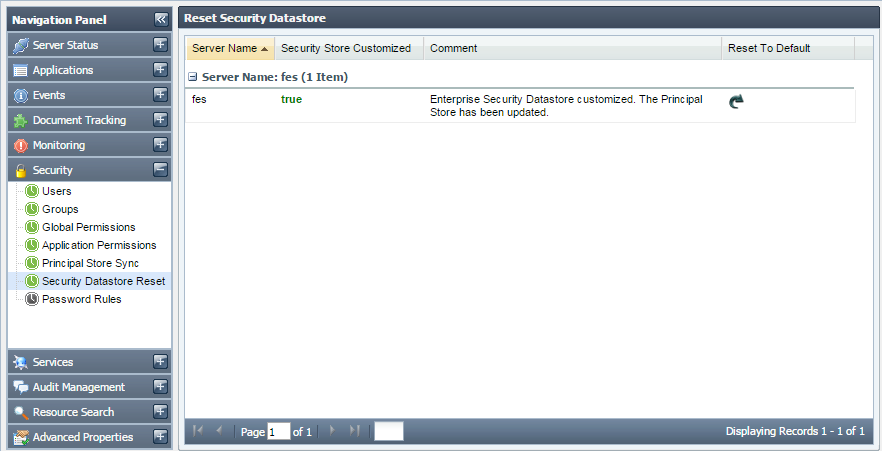
Figure 40: Security Datastore Reset
...
This tab shows the validation and strength rules that are used for matching the passwords or determining their strengths. This tab allows you to add new rules or remove an existing one. By default, no validation rules are provided.
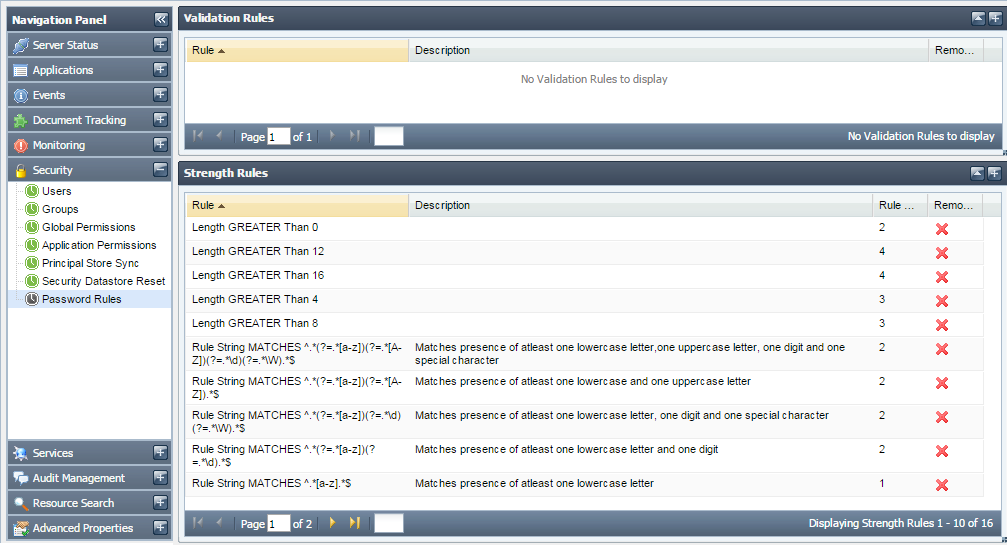
Figure 41: Password Rules
...
The Services tab shows the details of the event processes deployed as Web Services. You can view the status of web service either online or offline and has the option of enabling or disabling this option. You can also test RESTful deployed from the dashboard.
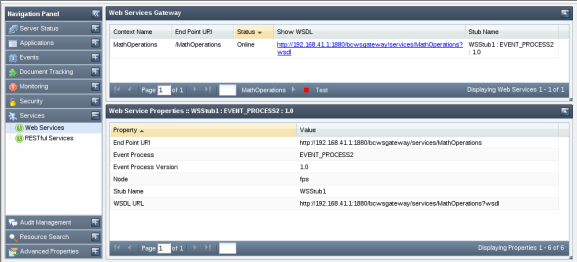
Figure 42: Web Services - Event process
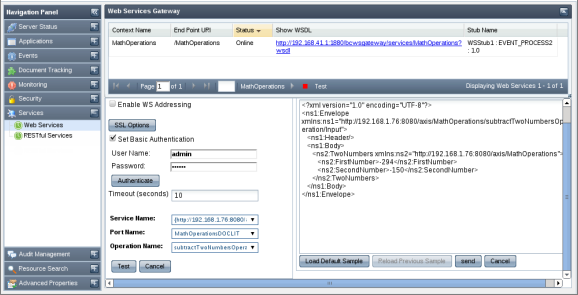
Figure 43: Web Services tab
...
In this view, you can view/edit available audit policies. These policies define the actions that will be audited by the system. In a fresh installation, all policies are in passive state, meaning none of the action is audited. You can selectively enable the actions that they want to audit.

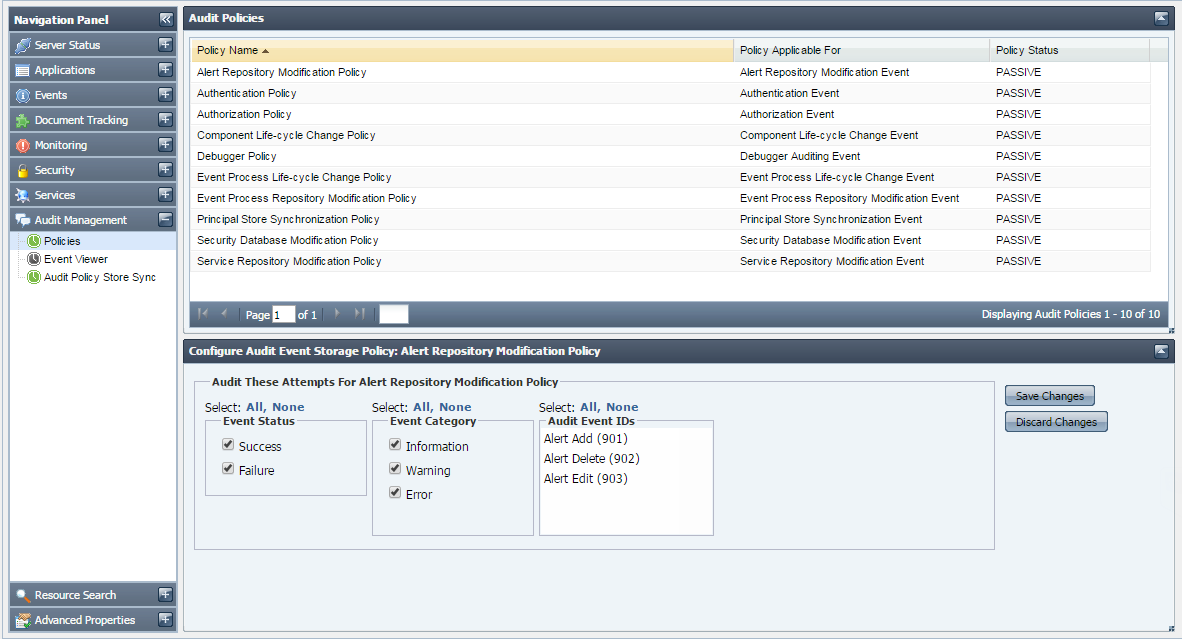
Figure 44: Policies
...
This view shows audit events based on the specified search criteria's specified by you. A comprehensive list of audit event filters is available to refine the audit events as per your requirement. This view also allows saving search preferences for later use, thus avoiding the painful task of creating audit filters each time you need to search. Below is a snapshot of Event Viewer page rendered after searching for certain audit events.
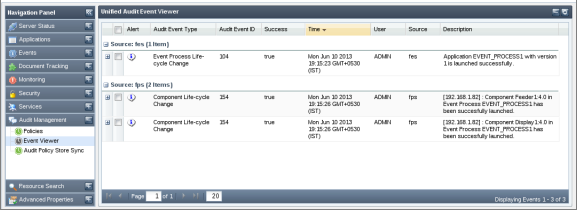
Figure 45: Event Viewer
...
This view shows the result of synchronization of audit policy store operation (See image below). A synchronized audit policy store means that the same audit policies (as in Enterprise Server) are active in peer servers as well. If stores are not synchronized, the status field will display 'false' and the reason for which the synchronization not achieved will be displayed under Comment column. You can force re-synchronization of audit policies with a particular peer server by clicking on the image shown under 'Synchronize' column.

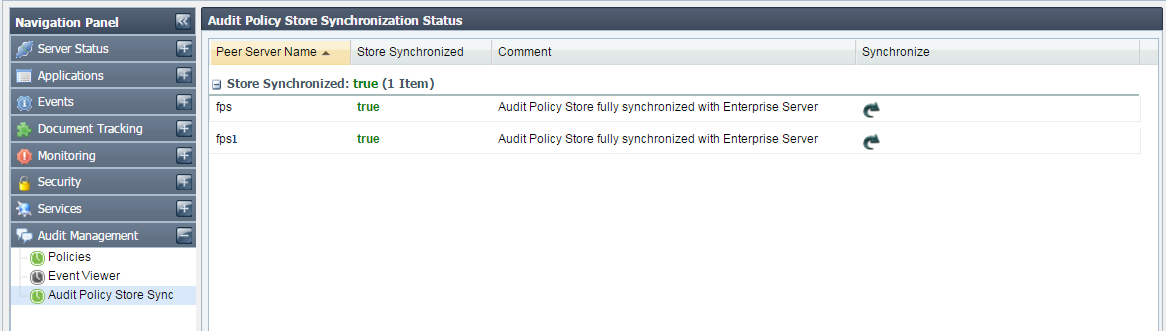
Figure 46: Audit Policy Store Synchronization
...
- Application View
- Component View
- Resource View

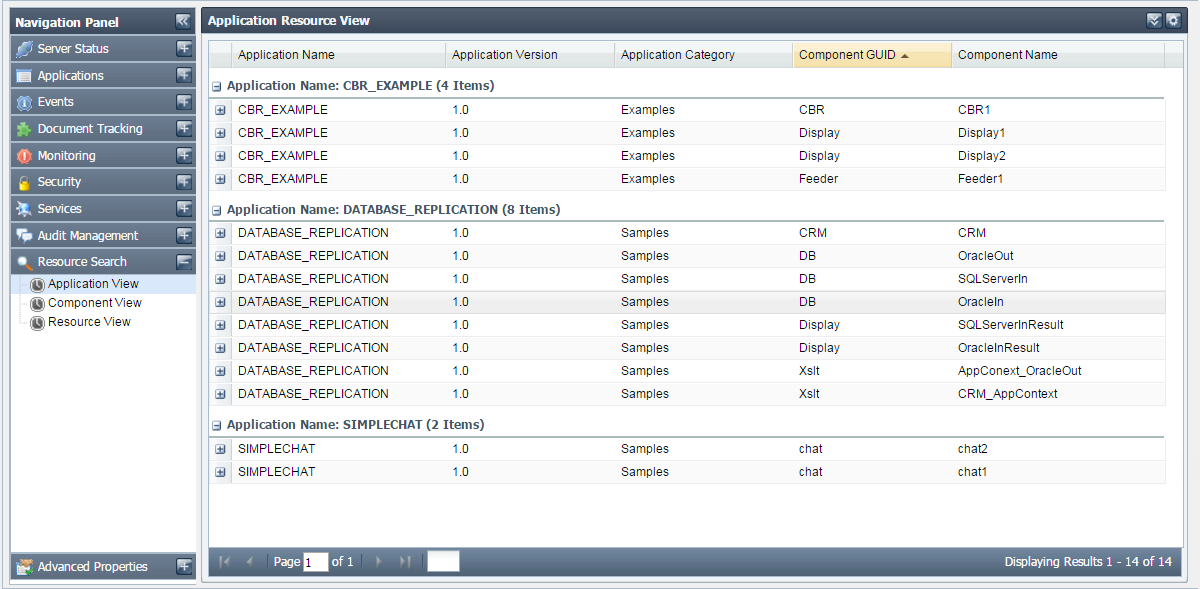
Figure 47: Searching configured resources based on application view

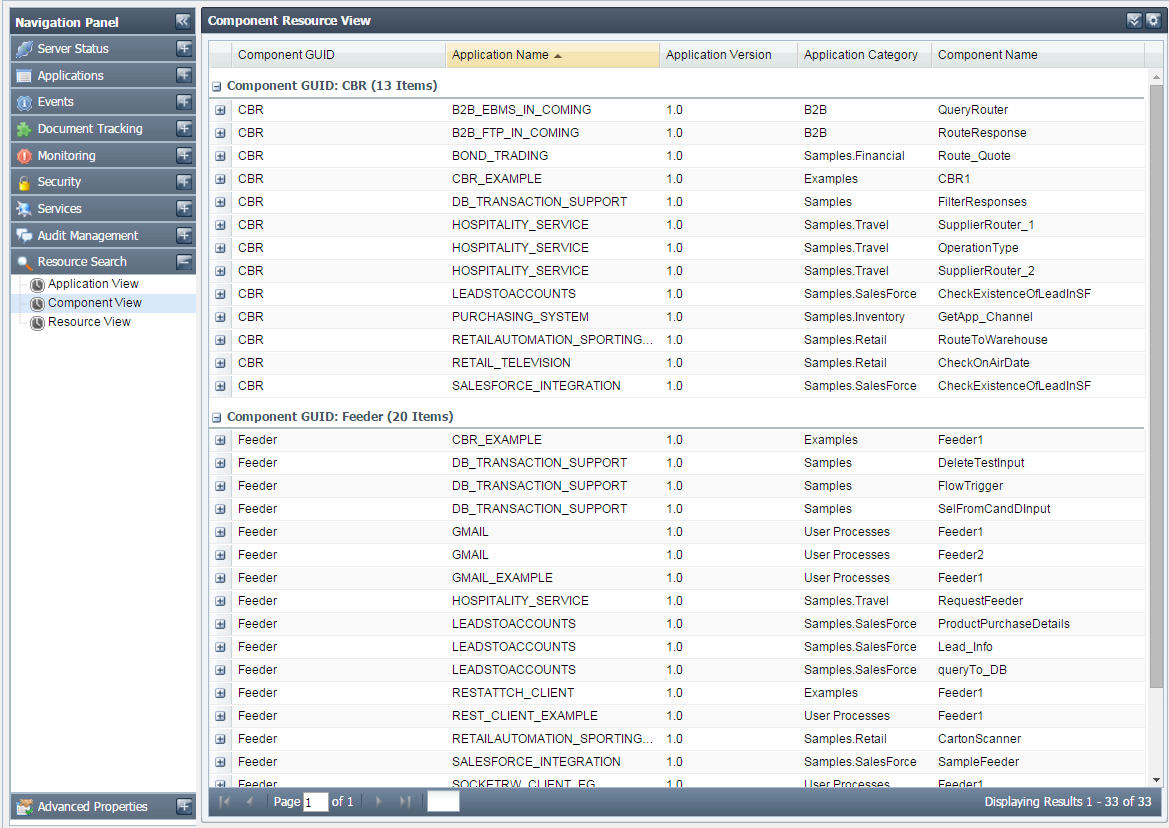
Figure 48: Searching configured resources based on component view

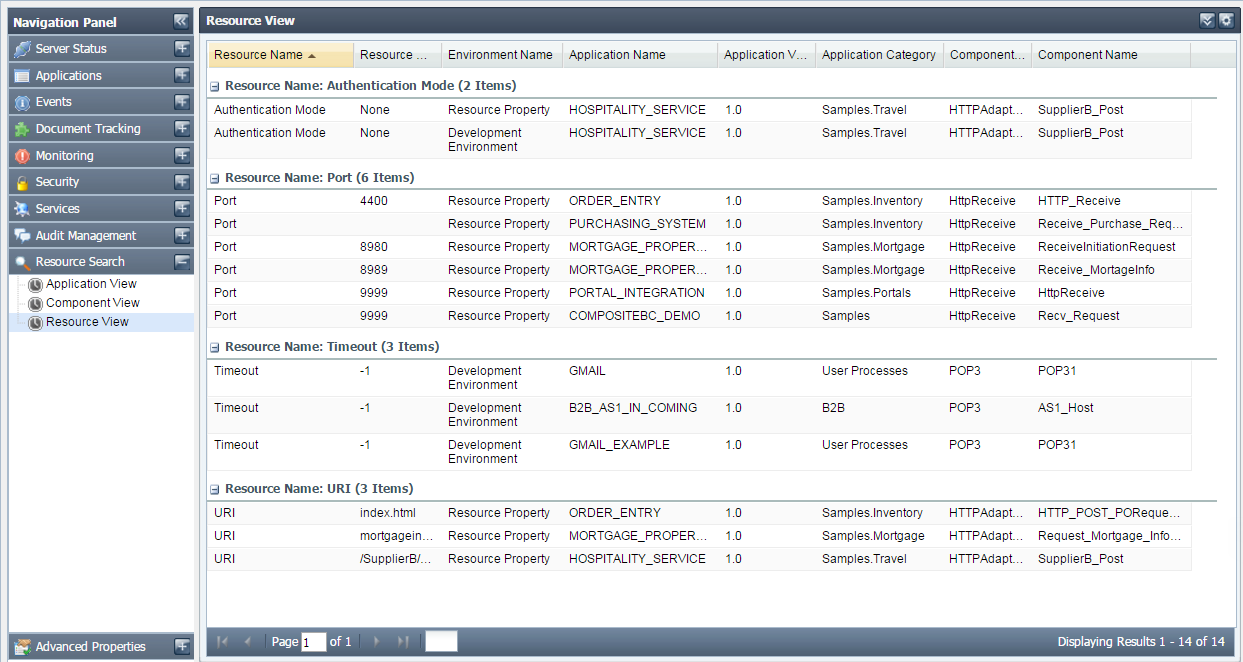
Figure 49: Searching configured resources based on resource view
...
This tab allows you to change values of frequently used server properties from Dashboard.

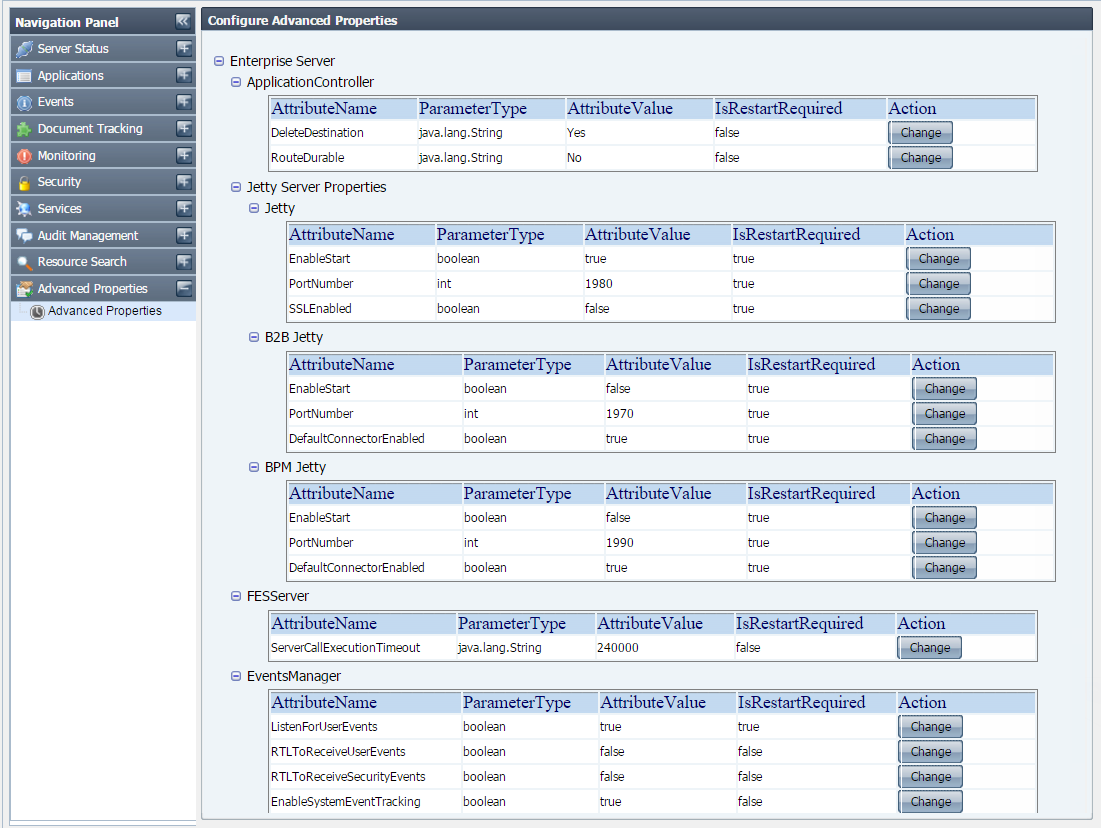
Figure 50: Advanced Properties
...
| Note |
|---|
If the restart required is true for the attribute. Then server needs to be restarted to get that value into effect. |
Figure 51: Change Attribute Value
...