...
The configuration for each algorithm is mentioned in the sections below.
DES
...
Decryption Algorithm Configuration
For DES, the configuration panel is as shown in Figure 2. Set the following fields accordingly.
- Encryption Key: Specify key which is used to encrypt the incoming data. Specify 32 digit key for AES256, 16 digit key for AES128, 16 digit key for DES, 24 digit key for TripleDES, 5 digit key for RC2_40, 8 digit key for RC2_64 and 16 digit key for RC2_128
- Allow Padding: Choose yes to allow padding to the key to make exactly the value required for the mentioned algorithm. It has to be chosen only when we know that the encrypted data key is also padded.
- Transformation: Transformation always includes the name of a cryptographic algorithm (e.g., AES), and may be followed by a feedback mode and padding scheme.
AES256, AES192, AES128, TripleDES
...
Decryption Algorithm configurations
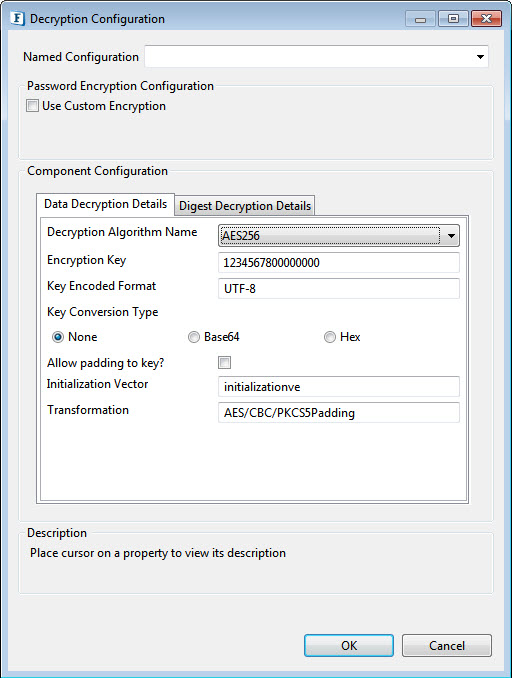
Figure 3: AES256 , AES192 , AES128,TripleDES Encryption Decryption configuration
Set the Encryption key and the Padding key details similar to the DES algorithm.
- Key Encoded Format: Specify appropriate encoding format for the key. Examples: (UTF-8), (ISO-8859-1).
- Key Conversion Type: Select Key Conversion Type in the following ways :
None: Select if the Encryption key is a simple string.
Base64: Select if the Encryption key is Base64 Encoded.
Hex: Select if the Encryption key is Hexadecimal Encoded.
Allow padding to key: Enable this property to allow padding to the key to make exactly the value required for the mentioned algorithm. It has to be chosen only when the encrypted data key is also padded.
Note This button will be disabled in the case of Base64 and Hex.
- InitializationVector: Mention the unique 64-bit input used in the encryption.
RC2_40, RC2_64,RC2_128
...
Decryption Algorithm Configurations
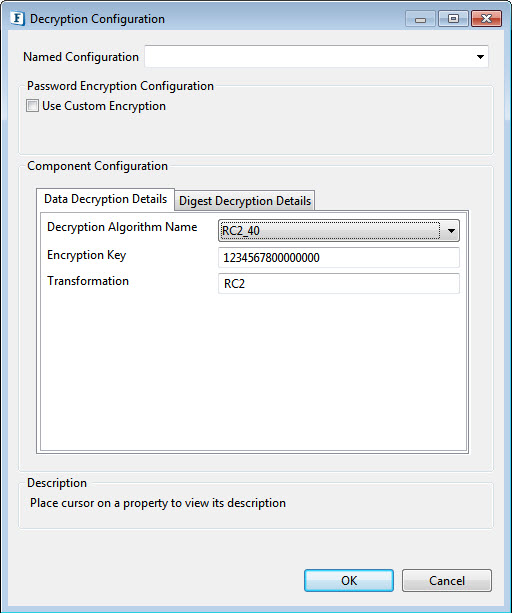
Figure 4: RC2_40, RC2_64,RC2_128 Algorithm EncryptionDecryption
Provide the encryption decryption in the same way as for the DES algorithm.
PGP
...
Decryption Configuration
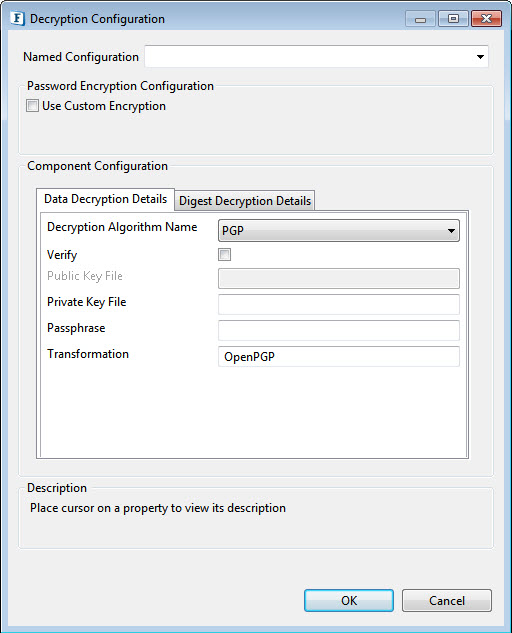
Figure 5: PGP, PGP_RFC4880 Algorithm EncryptionDecryption
- Verify: Select this option to sign the message when the algorithm used is PGP.
- Public Key File: Specify public key file used in case of PGP Algorithm
- Private Key File: Specify private key file used in case of PGP Algorithm
- Passphrase: Required for signing in case of PGP algorithm.
RSA
...
Decryption Configuration
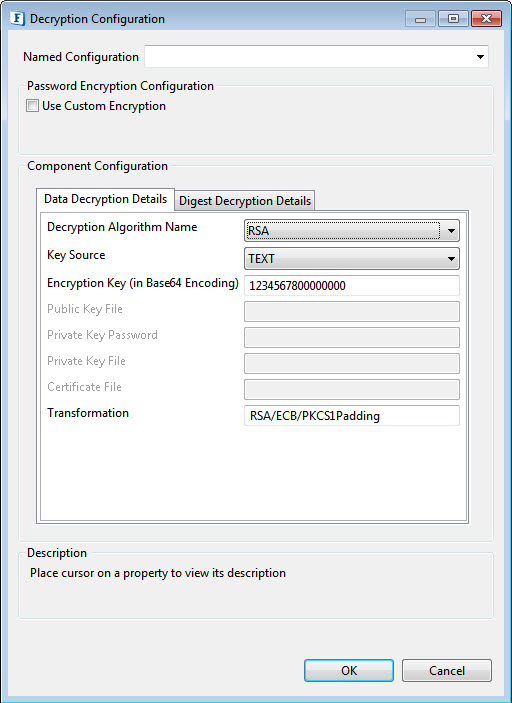
Figure 6: RSA Algorithm Encryption Decryption
Key Source: There are four options under Key Source :
- Text: This requires the Encryption Decryption Key details
- Encryption Key: Specify the appropriate Encryption Key for the selected algorithm to be used to decrypt the incoming data..
- PublicKeyFile: The public Key File field has to be filled for this.
- Public Key File: Provide the file containing the public key.
- PrivateKeyFile: The Private Key Password and the Private Key File are the active fields under this.
- Private Key password: Provide the private key password.
- Private Key File: Provide the file containing the Private Key.
- Certificate: Certificate File is the active field when the key source is Certificate.
- Certificate File: provide the path of the X509 Certificate.
...
Functional Demonstration
Scenario 1
Encryption Decryption of data received from the input.
...