...
This tab shows you details of Users currently registered in the Fiorano network. The actions that can be undertaken in this tab include creating new users, deleting an existing user or changing password for an existing user, provided that you have the proper User Permissions to do so.

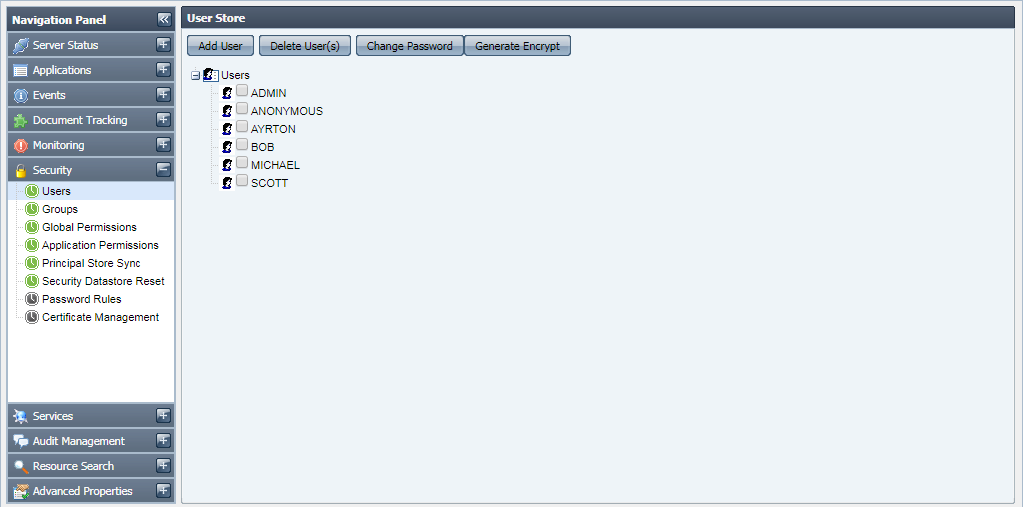
Figure 40: Users
...
This tab shows the groups registered in the Fiorano network. Groups allow grouping users together and applying actions on them together. The actions that can be undertaken in this tab include creating new groups, deleting/editing an existing group, provided that you have proper User Permissions to do so.

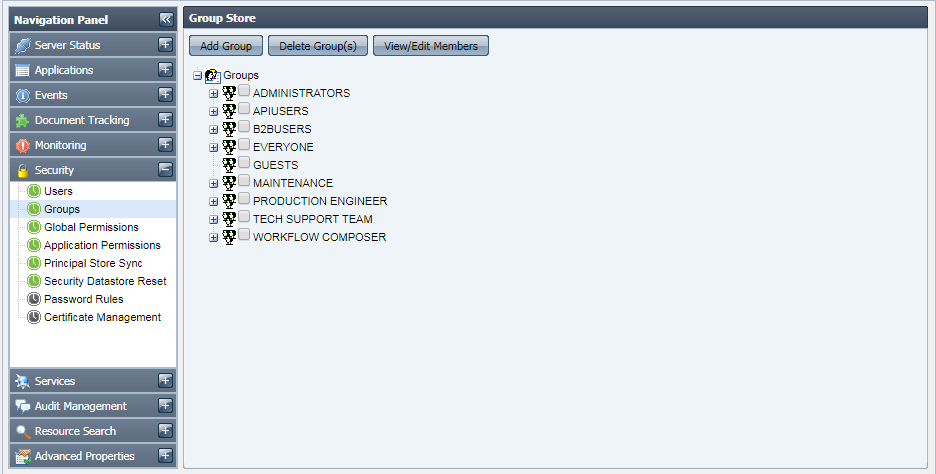
Figure 41: Groups
...
This tab shows the global permissions that are currently available in the Fiorano network. This tab allows you to edit or specify the users for whom these permissions will be applicable, provided that you have proper User Permissions to do so.

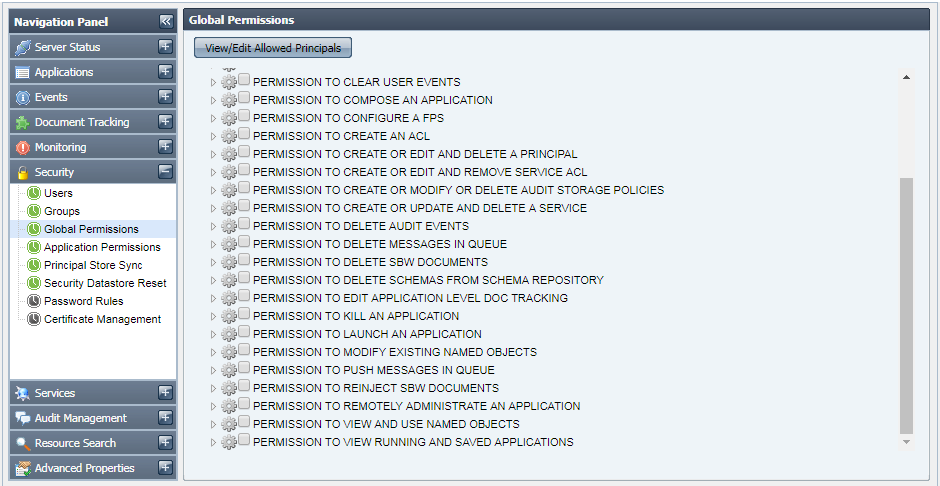
Figure 42: Global Permissions
...
| Info |
|---|
Application level permissions override global level permissions. For example, if a user is given launch permission for applications in global permissions, but for a particular application, he/she is not granted the permission to launch that application, then the user will not be allowed to launch that particular application. |

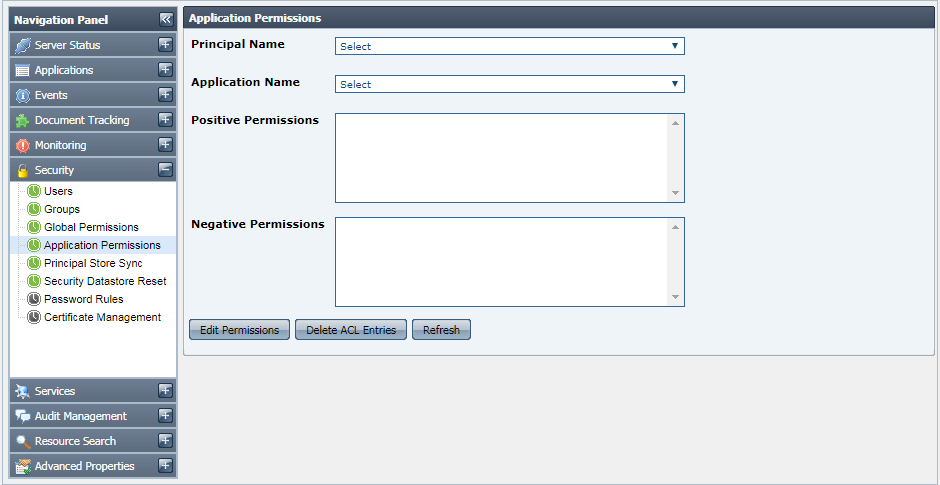
Figure 43: Application Permissions
...
This tab shows the principal store synchronization status for the connected peers. This also allows you to synchronize the store for a peer.

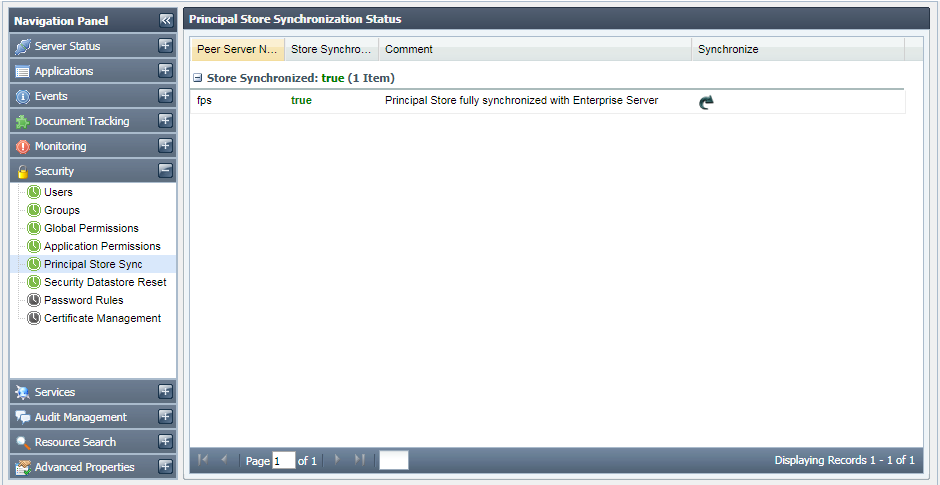
Figure 44: Principal Store Sync
...
This tab shows the Security Datastore of the Enterprise Network. It also allows the authorized user to reset the entire Security Datastore viz. the Principals and the ACLs to system default.

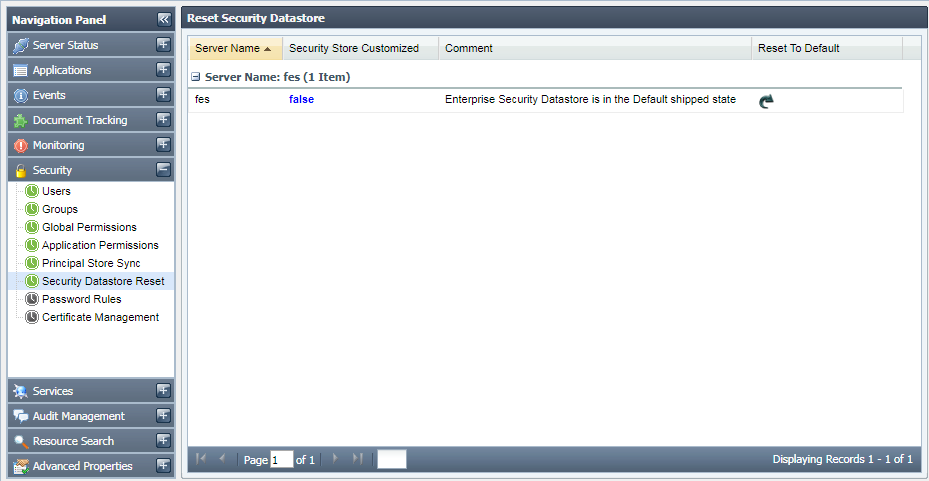
Figure 45: Security Datastore Reset
...
This tab shows the validation and strength rules that are used for matching the passwords or determining their strengths. This tab allows you to add new rules or remove an existing one. By default, no validation rules are provided.

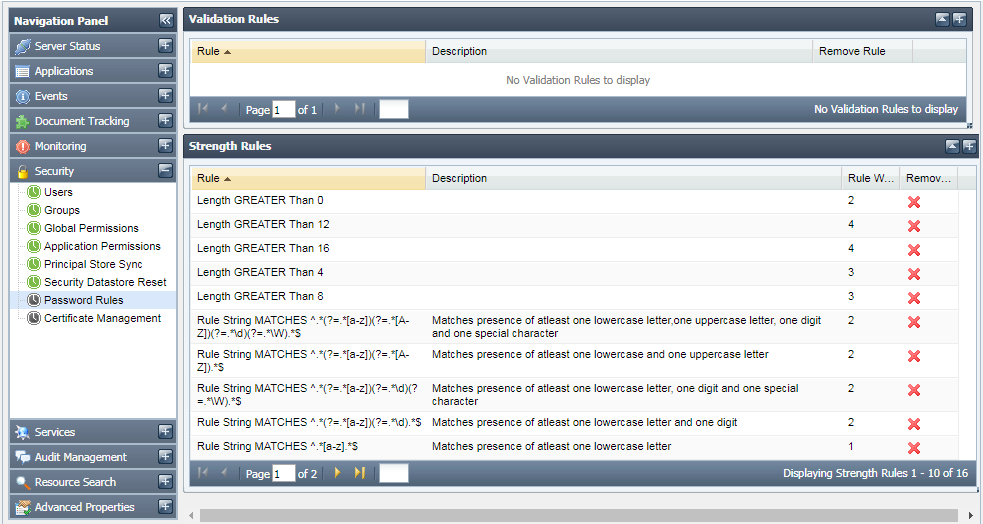
Figure 46: Password Rules
...
| Tip |
|---|
While starting peer server, the port for WMT will be listed as the Dashboard Listening Port. |