...
- Open the profile for offline editing through the Profile Manager using Studio by clicking on the Profile Manager pane, explained in the Pinging section.
- Modify the Implementation property of the ACL Manager and the Principal Manager to LDAP. For more information on how to modify ACL Manager and Principal Manager refer to the section Modifying ACL Manager Implementation and Modifying ACL and Principal Manager Implementation.
- Configure the Principal Manager as per the Directory server in use. A sample configuration for the Netscape Directory Server is shown in the figure Directory Server Settings.
- Right-click on the FioranoMQ node and select Save from the pop-up menu.
...
Sample Configuration – Netscape Directory Server
Setting the Name
The 'name' is the name of the admin of the LDAP server, since the Initial Context may only be started by the Admin.
...
| Code Block |
|---|
LdapSecurityAuthentication = Simple LDAP User and Group Object classes |
...
Sample Configuration – ApacheDS1.5.4
| Note |
|---|
The steps mentioned here require the installation of the Apache Directory Studio. |
...
Setting up the Directory Service
To setup the directory service, the steps below are to be performed:
- Stop any running instance of ApacheDS.
- Take a backup of server.xml
/var/lib/apacheds-1.5.4/default/conf/server.xml
(Default path: If the DS instances were installed in a location different, server.xml will be available inside the directory at that location.) - Modify server.xml by adding the line below within the tag </partitions> ... </partitions>
<jdbmPartition id="fiorano" cacheSize="100" suffix="o=fiorano,c=US" optimizerEnabled="true" syncOnWrite="true"/> - Run apacheds
/etc/init.d/apachedsstart - Login through the Apache Directory Studio.
- User: uid=admin,ou=system. (Default)
- Password: secret. (Default)
Import the LDIF content below using Apache Directory Studio. (Menu: LDAP -> New LDIF File)
Code Block dn: o=fiorano,c=us objectclass: top objectClass: organization o: fiorano dn: cn=FMQServerConfigFiles,o=fiorano,c=us objectclass: top objectClass: organizationalRole cn: FMQServerConfigFiles dn: cn=FioranoMQUsers,o=fiorano,c=us objectClass: top objectClass: organizationalRole cn: FioranoMQUsers dn: cn=FioranoMQGroups,o=fiorano,c=us objectClass: top objectClass: organizationalRole cn: FioranoMQGroups dn: cn=ACL,o=fiorano,c=US objectclass: top objectClass: organizationalRole cn: ACL dn: cn=FMQRoot,o=fiorano,c=us objectClass: inetOrgPerson objectClass: organizationalPerson objectClass: person objectClass: top cn: FMQRoot cn: system administrator sn: administrator displayname: Directory Superuser userpassword:: c2VjcmV0
- Re-login through Apache Directory Studio to see the added children.
...
Setting up the profile for use with ApacheDS1.5.4
| Note |
|---|
Make sure that the steps mentioned in section 7.9 have been completed before moving on to the steps listed below: |
- Open the profile for off-line editing through the Profile Manager using Studio, as explained in section 4.8.1 How to Enable Pingingthe Modifying ACLManager Implementation section ine the Working with ACL based Security page.
- Reset all properties except the LdapProviderUrl to their original values.
- In the LDAP Provider URL, the port number is 10389 and the ip address is that of the server that running ApacheDS.
...
Sample LDAP Configuration for ACLs, Users and Groups
...
Configuration for Users and Groups
Here is an example of how FioranoMQ profile can be configured to store principal realms (users and groups) related to the FioranoMQ Server.
...
- After opening the profile in Fiorano Studio for offline editing and changing the Principal Manager implementation to LDAP as explained in section Modifying ACL and Principal Manager Implementation, change the following node: Fiorano > security > PrincipalManager > LdapPrincipalManager

Figure: LDAP_Conf 1
...
Once the FioranoMQ is configured to use LDAP to store users and groups and the server is started, it sequentially creates them. The way in which the users and groups are stored in the LDAP-provider is illustrated using the following figure.
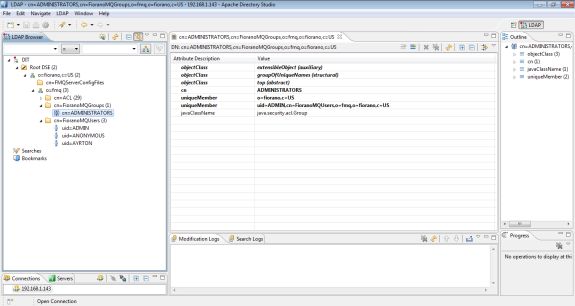
Figure: LDAP_Browser 1
...
Configuration for Access Control Lists (ACLs)
Here is an example of how FioranoMQ profile can be configured to store Access Control Lists (ACLs) related to the FioranoMQ Admin Objects like Queues, Topics, Connection Factories and other ACLs related to Lookup, AdminConnection etc. in the LDAP-provider. As an example, the view of how the ACLs are stored in the LDAP provider is extracted using the Apache Directory Studio.
...
- After opening the profile in Fiorano Studio for offline editing and changing the ACL implementation to LDAP as explained in section 7.4 in the Modifying ACLManager Implementation, section ine the Working with ACL based Security page; change the following node: Fiorano > security > AclManager > LdapBasedAclManager
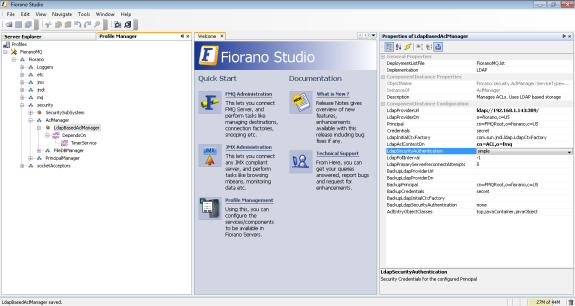
Figure: LDAP_Conf2.png goes here
...