...
| Expand | ||
|---|---|---|
| ||
|
TCP with JSSE Security
- Launch the Fiorano Studio for offline configuration of the FioranoMQ server.
- Select Tools > ConfigureProfile from the menu bar, and open the profile needed. Navigate to %selectedProfile% > Fiorano > SocketAcceptors >
...
- Port-1 > ConnectionManager in the ServerExplorer.

- Change the Protocol property to SUN_SSL
Change the UseSystemPropsForSSL to true (Optional)
...
Note The public/private keys and/or certificates used by the FioranoMQ Server can be loaded by specifying the related system properties, or by installing the appropriate security managers which can load the certificates. Please see the note at the start of Section 4.5.1.
- Navigate to %selectedProfile% > Fiorano > etc > FMQConfigLoader. Right-click on FMQConfigLoader, and select Add Attribute from the pop-up menu. Add an additional attribute with the name SSLEnabled and with a value that is 'true'.
...

Navigate to %selectedProfile% > Fiorano > socketAcceptors > port-1 > ConnectionManager. Check the default value of property ManagerClassName. Ensure that the default value of ManagerClassName is fiorano.jms.ex.sm.def.DefaultJSSESecurityManager. (Optional)
...
Note This parameter is deprecated. Alternatively, in order to load the KeyStore and TrustStore, for initializing the context in which SSL Sockets are created, corresponding system properties should be set,
...
and UseSystemPropsForSSL
...
should be set to true.

- Navigate to Fiorano > jmx > connector > JMSBasedJMXConnector2, and set the following properties to allow the JMSConnector to connect to the secure server.
- Protocol: TCP
- SecurityManagerClass: fiorano.jmx.connector.fmq.security.JSSESecurityManager
- SecurityProtocol: SUN_SSL

- Right-click the FioranoMQ domain in the Profile Manager, and select the Save option from the pop-up menu. Changes are saved in the Configs.xml file.

Clear the existing database using script ClearDB.bat located in %FIORANO_HOME%\fmq\bin directory.
Code Block ClearDB.bat %selectedProfile%Start the Server again using script file fmq.bat located in %FIORANO_HOME%\fmq\bin directory.
Code Block fmq.bat –profile %selectedProfile%
The server starts accepting connections on TCP in the SSL (JSSE) mode.
HTTPwithJSSESecurity
- Launch the Fiorano Studio for offline configuration of the FioranoMQ server.
- Select Tools > Configure Profile from the menu bar, and open the profile needed. Navigate to %selectedProfile% > Fiorano > SocketAcceptors > Port1 Port-1 > ConnectionManager.
- Change the protocol property from TCP to HTTPS_SUN.
- Navigate to %selectedProfile% > Fiorano > etc > FMQConfigLoader. Right-click on FMQConfigLoader and select Add Attribute from the pop-up menu. Add an additional attribute with the name SSLEnabled and with the value 'true'.
- Navigate to %selectedProfile% > Fiorano > socketAcceptors > port-1 > ConnectionManager. Check the default value of property ManagerClassName. Ensure that the default value of Security manager is fiorano.jms.ex.sm.def.DefaultJSSESecurityManager.
- Navigate to Fiorano > jmx > connector > JMSBasedJMXConnector2, and set the following properties to allow JMSConnector to connect to the secure server.
- Protocol: HTTP
- SecurityManagerClass: fiorano.jmx.connector.fmq.security.JSSESecurityManager
- SecurityProtocol: SUN_SSL
- Right-click the FioranoMQ domain in the Server Explorer, and select the Save option from the pop-up menu. Changes are saved in the Configs.xml file.
- Clear the existing database, using script ClearDB.bat, located in the %FIORANO_HOME%\fmq\bin directory.
...
- A similar procedure is followed to enable SSL for FES/FPS servers. For FPS profiles, the Protocol, SecurityProtocol and SecurityManagerClass properties for Fiorano > jmx >Engine > Engine > ClientJMXEngine also need to be changed.
- When FioranoMQ server is running with HTTPS_SUN protocol, pinging is enabled at the server. Also, the client connecting to the server must enable ping.
...
The server, by default, uses fiorano.jms.ex.sm.def.DefaultJSSESecurityManager class as a Security Manager. This value can be modified from the Studio using Profile Manger at:
Profiles ->FioranoMQ->socketAcceptors->port-1->ConnectionManager> FioranoMQ > socketAcceptors > port-1 > ConnectionManager[properties] ->ManagerClassName> ManagerClassName
A sample Security Manager Class is displayed below.
JSSESecurityManager.java
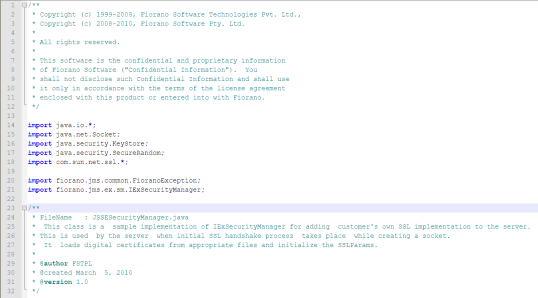
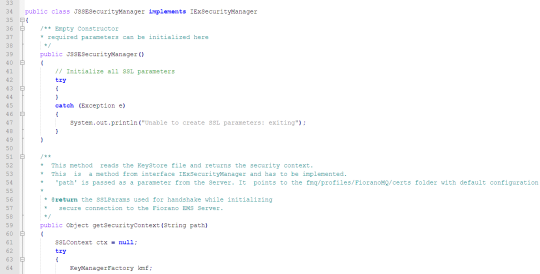
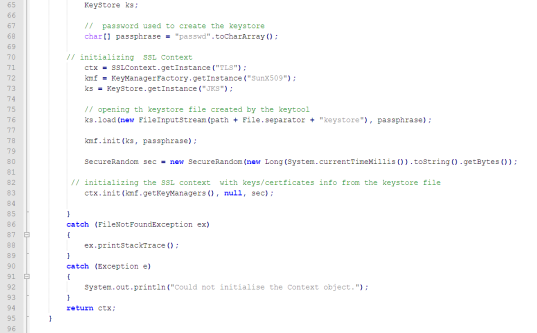
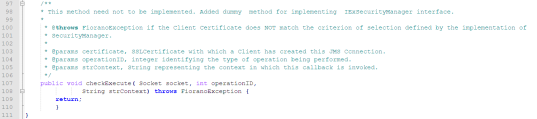
4.5.3.1 Compiling the Security Manager
...
javax.net.ssl.trustStore=<path - is the path to the keystore>

4.5.4 Client Side Configuration
...
| Code Block |
|---|
java -jar portecle.jar |
![]()
- Open the keystore that needs to be converted to the .PEM format using Portcele. All the information related to the certificate can be viewed here.
- Navigate to File >> OpenKeyStoreFile. Choose the keystore that was created.
- Enter the password provided at the time of the creation of the keystore.
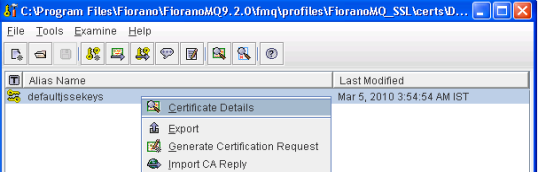
4. Right-click on certificate, and choose export. Select the export 'type' as "Private Key and Certificates", and the export format as "PEM Encoding".
...